



A Framework That Works
Cybersecurity isn’t just the responsibility of a dedicated team anymore. Whether you’re an engineer, a product owner, or part of the executive suite, your day-to-day decisions have a direct impact on your organization’s security. That was the clear message from the expert panel featured in our webinar, Cybersecurity Skills: A Framework That Works — now available to watch on demand.
Leaders from IBM, Intel, Linux Foundation Education and the Open Source Security Foundation (OpenSSF) share real-world insights on how their organizations are tackling one of today’s biggest challenges: upskilling the entire workforce in security. The panelists discussed the new Cybersecurity Skills Framework, an open, flexible tool designed to help teams identify the right skills for the right roles — and actually get started improving them. It’s practical, customizable, and already helping global organizations raise their security posture.
In the webinar, you’ll hear how to:
The conversation is packed with actionable advice, whether you’re building a security training program or just want to understand where you or your team stands.
🎥Access the Cybersecurity Skills, Simplified Webinar
BONUS: Receive a 30% Discount for any Security-Related Course, Certification or Bundle Just for Watching
Need to Close the Skills Gap Across Your Team or Enterprise?

Foundation furthers mission to enhance the security of open source software
DENVER – OpenSSF Community Day North America – June 26, 2025 – The Open Source Security Foundation (OpenSSF), a cross-industry initiative of the Linux Foundation that focuses on sustainably securing open source software (OSS), welcomes six new members from leading technology and security companies. New general members include balena, Buildkite, Canonical, Trace Machina, and Triam Security and associate members include Erlang Ecosystem Foundation (EEF). The Foundation also presents the Golden Egg Award during OpenSSF Community Day NA 2025.
“We are thrilled to welcome six new member companies and honor existing contributors during our annual North America Community Day event this week,” said Steve Fernandez, General Manager at OpenSSF. “As companies expand their global footprint and depend more and more on interconnected technologies, it is vital we work together to advance open source security at every layer – from code to systems to people. With the support of our new members, we can share best practices, push for standards and ensure security is front and center in all development.”
The OpenSSF continues to shine a light on those who go above and beyond in our community with the Golden Egg Awards. The Golden Egg symbolizes gratitude for awardees’ selfless dedication to securing open source projects through community engagement, engineering, innovation, and thoughtful leadership. This year, we celebrate:
Their efforts have made a lasting impact on the open source security ecosystem, and we are deeply grateful for their continued contributions.
OpenSSF is supported by more than 3,156 technical contributors across OpenSSF projects – providing a vendor-neutral partner to affiliated open source foundations and projects. Recent project updates include:
New and existing OpenSSF members are gathering this week in Denver at the annual OpenSSF Community Day NA 2025. Join the community at upcoming 2025 OpenSSF-hosted events, including OpenSSF Community Day India, OpenSSF Community Day Europe, OpenSSF Community Day Korea, and Open Source SecurityCon 2025.
“At balena, we understand that securing edge computing and IoT solutions is critical for all companies deploying connected devices. As developers focused on enabling reliable and secure operations with balenaCloud, we’re deeply committed to sharing our knowledge and expertise. We’re proud to join OpenSSF to contribute to open collaboration, believing that together we can build more mature security solutions that truly help companies protect their edge fleets and raise collective awareness across the open-source ecosystem.”
– Harald Fischer, Security Aspect Lead, balena
“Joining OpenSSF is a natural extension of Buildkite’s mission to empower teams with secure, scalable, and resilient software delivery. With Buildkite Package Registries, our customers get SLSA-compliant software provenance built in. There’s no complex setup or extra tooling required. We’ve done the heavy lifting so teams can securely publish trusted artifacts from Buildkite Pipelines with minimal effort. We’re excited to collaborate with the OpenSSF community to raise the bar for open source software supply chain security.”
– Ken Thompson, Vice President of Product Management, Buildkite
“Protecting the security of the open source ecosystem is not an easy feat, nor one that can be tackled by any single industry player. OpenSSF leads projects that are shaping this vast landscape. Canonical is proud to join OpenSSF on its mission to spearhead open source security across the entire market. For over 20 years we have delivered security-focused products and services across a broad spectrum of open source technologies. In today’s world, software security, reliability, and provenance is more important than ever. Together we will write the next chapter for open source security frameworks, processes and tools for the benefit of all users.”
– Luci Stanescu, Security Engineering Manager, Canonical
“Starting in 2024, the EEF’s Security WG focused community resources on improving our supply chain infrastructure and tooling to enable us to comply with present and upcoming cybersecurity laws and directives. This year we achieved OpenChain Certification (ISO/IEC 5230) for the core Erlang and Elixir libraries and tooling, and also became the default CVE Numbering Authority (CNA) for all open-source Erlang, Elixir and Gleam language packages. Joining the OpenSSF has been instrumental in connecting us to experts in the field and facilitating relationships with security practitioners in other open-source projects.”
– Alistair Woodman, Board Chair, Erlang Ecosystem Foundation
“Trace Machina is a technology company, founded in September 2023, that builds infrastructure software for developers to go faster. Our current core product, NativeLink, is a build caching and remote execution platform that speeds up compute-heavy work. As a company we believe both in building our products open source whenever possible, and in supporting the open source ecosystem and community. We believe open source software is a crucial philosophy in technology, especially in the security space. We’re thrilled to join the OpenSSF as a member organization and to continue being active in this wonderful community.”
– Tyrone Greenfield, Chief of Staff, Trace Machina
“Triam Security is proud to join the Open-Source Security Foundation to support its mission of strengthening the security posture of critical open source software. As container security vulnerabilities continue to pose significant risks to the software supply chain, our expertise in implementing SLSA Level 3/4 controls and building near-zero CVE solutions through CleanStart aligns perfectly with OpenSSF’s supply chain security initiatives. We look forward to collaborating with the community on advancing SLSA adoption, developing security best practices, improving vulnerability management processes, and promoting standards that enhance the security, transparency, and trust in the open-source ecosystem.”
– Biswajit De, CTO, Triam Security
About the OpenSSF
The Open Source Security Foundation (OpenSSF) is a cross-industry organization at the Linux Foundation that brings together the industry’s most important open source security initiatives and the individuals and companies that support them. The OpenSSF is committed to collaboration and working both upstream and with existing communities to advance open source security for all. For more information, please visit us at openssf.org.
Media Contact
Natasha Woods
The Linux Foundation

Welcome to the June 2025 edition of the OpenSSF Newsletter! Here’s a roundup of the latest developments, key events, and upcoming opportunities in the Open Source Security community.
 The recent Tech Talk, “CRA-Ready: How to Prepare Your Open Source Project for EU Cybersecurity Regulations,” brought together open source leaders to explore the practical impact of the EU’s Cyber Resilience Act (CRA). With growing pressure on OSS developers, maintainers, and vendors to meet new security requirements, the session provided a clear, jargon-free overview of what CRA compliance involves.
The recent Tech Talk, “CRA-Ready: How to Prepare Your Open Source Project for EU Cybersecurity Regulations,” brought together open source leaders to explore the practical impact of the EU’s Cyber Resilience Act (CRA). With growing pressure on OSS developers, maintainers, and vendors to meet new security requirements, the session provided a clear, jargon-free overview of what CRA compliance involves.
Speakers included CRob (OpenSSF), Adrienn Lawson (Linux Foundation), Dave Russo (Red Hat), and David A. Wheeler (OpenSSF), who shared real-world examples of how organizations are preparing for the regulation, even with limited resources. The discussion also highlighted the LFEL1001 CRA course, designed to help OSS contributors move from confusion to clarity with actionable guidance.
Watch the session here.

The Open Source Technology Improvement Fund (OSTIF) addresses a critical gap in open source security by conducting tailored audits for high-impact OSS projects often maintained by small, under-resourced teams. Through its active role in OpenSSF initiatives and strategic partnerships, OSTIF delivers structured, effective security engagements that strengthen project resilience. By leveraging tools like the OpenSSF Scorecard and prioritizing context-specific approaches, OSTIF enhances audit outcomes and fosters a collaborative security community. Read the full case study to explore how OSTIF is scaling impact, overcoming funding hurdles, and shaping the future of OSS security.
✨GUAC 1.0 is Now Available

Discover how GUAC 1.0 transforms the way you manage SBOMs and secure your software supply chain. This first stable release of the “Graph for Understanding Artifact Composition” platform moves beyond isolated bills of materials to aggregate and enrich data from file systems, registries, and repositories into a powerful graph database. Instantly tap into vulnerability insights, license checks, end-of-life notifications, OpenSSF Scorecard metrics, and more. Read the blog to learn more.
✨Maintainers’ Guide: Securing CI/CD Pipelines After the tj-actions and reviewdog Supply Chain Attacks
CI/CD pipelines are now prime targets for supply chain attacks. Just look at the recent breaches of reviewdog and tj-actions, where chained compromises and log-based exfiltration let attackers harvest secrets without raising alarms. In this Maintainers’ Guide, Ashish Kurmi breaks down exactly how those exploits happened and offers a defense-in-depth blueprint from pinning actions to full commit SHAs and enforcing MFA, to monitoring for tag tampering and isolating sensitive secrets that every open source project needs today. Read the full blog to learn practical steps for locking down your workflows before attackers do.
✨From Sandbox to Incubating: gittuf’s Next Step in Open Source Security

gittuf, a platform-agnostic Git security framework, has officially progressed to the Incubating Project stage under the OpenSSF marking a major milestone in its development, community growth, and mission to strengthen the open source software supply chain. By adding cryptographic access controls, tamper-evident logging, and enforceable policies directly into Git repositories without requiring developers to abandon familiar workflows, gittuf secures version control at its core. Read the full post to see how this incubation will accelerate gittuf’s impact and how you can get involved.
✨Choosing an SBOM Generation Tool
With so many tools to build SBOMs, single-language tools like npm-sbom and CycloneDX’s language-specific generators or multi‐language options such as cdxgen, syft, and Tern, how do you know which one to pick? Nathan Naveen helps you decide by comparing each tool’s dependency analysis, ecosystem support, and CI/CD integration, and reminds us that “imperfect SBOMs are better than no SBOMs.” Read the blog to learn more.
✨OSS and the CRA: Am I a Manufacturer or a Steward?
The EU Cyber Resilience Act (CRA) introduces critical distinctions for those involved in open source software particularly between manufacturers and a newly defined role: open source software stewards. In this blog, Mike Bursell of OpenSSF breaks down what these terms mean, why most open source contributors won’t fall under either category, and how the CRA acknowledges the unique structure of open source ecosystems. If you’re wondering whether the CRA applies to your project or your role this post offers clear insights and guidance. Read the full blog to understand your position in the new regulatory landscape.

#33 – S2E10 “Bridging DevOps and Security: Tracy Ragan on the Future of Open Source”: In this episode of What’s in the SOSS, host CRob sits down with longtime open source leader and DevOps champion Tracy Ragan to trace her journey from the Eclipse Foundation to her work with Ortelius, the Continuous Delivery Foundation, and the OpenSSF. CRob and Tracy dig into the importance of configuration management, DevSecOps, and projects like the OpenSSF Scorecard and Ortelius in making software supply chains more transparent and secure, plus strategies to bridge the education gap between security professionals and DevOps engineers.
#32 – S2E09 “Yoda, Inclusive Strategies, and the Jedi Council: A Conversation with Dr. Eden-Reneé Hayes”: In this episode of What’s in the SOSS, host Yesenia Yser sits down with DEI strategist, social psychologist, and Star Wars superfan Dr. Eden-Reneé Hayes to discuss the myths around DEIA and why unlearning old beliefs is key to progress. Plus, stay for the rapid-fire questions and discover if Dr. Hayes is more Marvel or DC.
The Open Source Security Foundation (OpenSSF), together with Linux Foundation Education, provides a selection of free e-learning courses to help the open source community build stronger software security expertise. Learners can earn digital badges by completing offerings such as:
These are just a few of the many courses available for developers, managers, and decision-makers aiming to integrate security throughout the software development lifecycle.
Join us at OpenSSF Community Day Events in North America, India, Japan, Korea and Europe!
OpenSSF Community Days bring together security and open source experts to drive innovation in software security.
Connect with the OpenSSF Community at these key events:
Ways to Participate:
There are a number of ways for individuals and organizations to participate in OpenSSF. Learn more here.
You’re invited to…
We want to get you the information you most want to see in your inbox. Missed our previous newsletters? Read here!
Have ideas or suggestions for next month’s newsletter about the OpenSSF? Let us know at marketing@openssf.org, and see you next month!
Regards,
The OpenSSF Team

By Mihai Maruseac (Google), Eoin Wickens (HiddenLayer), Daniel Major (NVIDIA), Martin Sablotny (NVIDIA)
As AI adoption continues to accelerate, so does the need to secure the AI supply chain. Organizations want to be able to verify that the models they build, deploy, or consume are authentic, untampered, and compliant with internal policies and external regulations. From tampered models to poisoned datasets, the risks facing production AI systems are growing — and the industry is responding.
In collaboration with industry partners, the Open Source Security Foundation (OpenSSF)’s AI/ML Working Group recently delivered a model signing solution. Today, we are formalizing the signature format as OpenSSF Model Signing (OMS): a flexible and implementation-agnostic standard for model signing, purpose-built for the unique requirements of AI workflows.
Model signing is a cryptographic process that creates a verifiable record of the origin and integrity of machine learning models. Recipients can verify that a model was published by the expected source, and has not subsequently been tampered with.
Signing AI artifacts is an essential step in building trust and accountability across the AI supply chain. For projects that depend on open source foundational models, project teams can verify the models they are building upon are the ones they trust. Organizations can trace the integrity of models — whether models are developed in-house, shared between teams, or deployed into production.
Key stakeholders that benefit from model signing:
Model signing uses cryptographic keys to ensure the integrity and authenticity of an AI model. A signing program uses a private key to generate a digital signature for the model. This signature can then be verified by anyone using the corresponding public key. These keys can be generated a-priori, obtained from signing certificates, or generated transparently during the Sigstore signing flow.If verification succeeds, the model is confirmed as untampered and authentic; if it fails, the model may have been altered or is untrusted.
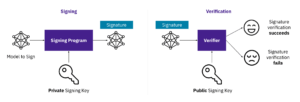
Figure 1: Model Signing Diagram
OMS is designed to handle the complexity of modern AI systems, supporting any type of model format and models of any size. Instead of treating each file independently, OMS uses a detached OMS Signature Format that can represent multiple related artifacts—such as model weights, configuration files, tokenizers, and datasets—in a single, verifiable unit.
The OMS Signature Format includes:
The OMS Signature File follows the Sigstore Bundle Format, ensuring maximum compatibility with existing Sigstore (a graduated OpenSSF project) ecosystem tooling. This detached format allows verification without modifying or repackaging the original content, making it easier to integrate into existing workflows and distribution systems.
OMS is PKI-agnostic, supporting a wide range of signing options, including:
This flexibility enables organizations to adopt OMS without changing their existing key management or trust models.
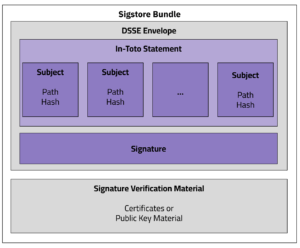
Figure 1. OMS Signature Format
As reference implementations to speed adoption, OMS offers both a command-line interface (CLI) for lightweight operational use and a Python library for deep integration into CI/CD pipelines, automated publishing flows, and model hubs. Other library integrations are planned.
Other examples, including signing using PKCS#11, can be found in the model-signing documentation.
This design enables better interoperability across tools and vendors, reduces manual steps in model validation, and helps establish a consistent trust foundation across the AI lifecycle.
The release of OMS marks a major step forward in securing the AI supply chain. By enabling organizations to verify the integrity, provenance, and trustworthiness of machine learning artifacts, OMS lays the foundation for safer, more transparent AI development and deployment.
Backed by broad industry collaboration and designed with real-world workflows in mind, OMS is ready for adoption today. Whether integrating model signing into CI/CD pipelines, enforcing provenance policies, or distributing models at scale, OMS provides the tools and flexibility to meet enterprise needs.
This is just the first step towards a future of secure AI supply chains. The OpenSSF AI/ML Working Group is engaging with the Coalition for Secure AI to incorporate other AI metadata into the OMS Signature Format, such as embedding rich metadata such as training data sources, model version, hardware used, and compliance attributes.
To get started, explore the OMS specification, try the CLI and library, and join the OpenSSF AI/ML Working Group to help shape the future of trusted AI.
Special thanks to the contributors driving this effort forward, including Laurent Simon, Rich Harang, and the many others at Google, HiddenLayer, NVIDIA, Red Hat, Intel, Meta, IBM, Microsoft, and in the Sigstore, Coalition for Secure AI, and OpenSSF communities.
 Mihai Maruseac is a member of the Google Open Source Security Team (GOSST), working on Supply Chain Security for ML. He is a co-lead on a Secure AI Framework (SAIF) workstream from Google. Under OpenSSF, Mihai chairs the AI/ML working group and the model signing project. Mihai is also a GUAC maintainer. Before joining GOSST, Mihai created the TensorFlow Security team and prior to Google, he worked on adding Differential Privacy to Machine Learning algorithms. Mihai has a PhD in Differential Privacy from UMass Boston.
Mihai Maruseac is a member of the Google Open Source Security Team (GOSST), working on Supply Chain Security for ML. He is a co-lead on a Secure AI Framework (SAIF) workstream from Google. Under OpenSSF, Mihai chairs the AI/ML working group and the model signing project. Mihai is also a GUAC maintainer. Before joining GOSST, Mihai created the TensorFlow Security team and prior to Google, he worked on adding Differential Privacy to Machine Learning algorithms. Mihai has a PhD in Differential Privacy from UMass Boston.
 Eoin Wickens, Director of Threat Intelligence at HiddenLayer, specializes in AI security, threat research, and malware reverse engineering. He has authored numerous articles on AI security, co-authored a book on cyber threat intelligence, and spoken at conferences such as SANS AI Cybersecurity Summit, BSides SF, LABSCON, and 44CON, and delivered the 2024 ACM SCORED opening keynote.
Eoin Wickens, Director of Threat Intelligence at HiddenLayer, specializes in AI security, threat research, and malware reverse engineering. He has authored numerous articles on AI security, co-authored a book on cyber threat intelligence, and spoken at conferences such as SANS AI Cybersecurity Summit, BSides SF, LABSCON, and 44CON, and delivered the 2024 ACM SCORED opening keynote.
 Daniel Major is a Distinguished Security Architect at NVIDIA, where he provides security leadership in areas such as code signing, device PKI, ML deployments and mobile operating systems. Previously, as Principal Security Architect at BlackBerry, he played a key role in leading the mobile phone division’s transition from BlackBerry 10 OS to Android. When not working, Daniel can be found planning his next travel adventure.
Daniel Major is a Distinguished Security Architect at NVIDIA, where he provides security leadership in areas such as code signing, device PKI, ML deployments and mobile operating systems. Previously, as Principal Security Architect at BlackBerry, he played a key role in leading the mobile phone division’s transition from BlackBerry 10 OS to Android. When not working, Daniel can be found planning his next travel adventure.
 Martin Sablotny is a security architect for AI/ML at NVIDIA working on identifying existing gaps in AI security and researching solutions. He received his Ph.D. in computing science from the University of Glasgow in 2023. Before joining NVIDIA, he worked as a security researcher in the German military and conducted research in using AI for security at Google.
Martin Sablotny is a security architect for AI/ML at NVIDIA working on identifying existing gaps in AI security and researching solutions. He received his Ph.D. in computing science from the University of Glasgow in 2023. Before joining NVIDIA, he worked as a security researcher in the German military and conducted research in using AI for security at Google.

Datadog, a leading cloud-scale observability and security platform, joined the Open Source Security Foundation (OpenSSF) as a Premier Member in July, 2024. With both executive leadership and deep technical involvement, Datadog has rapidly become a force in advancing secure open source practices across the industry.
GuardDog: Open Source Threat Detection
In early 2025, Datadog launched GuardDog, a Python-based open source tool that scans package ecosystems like npm, PyPI, and Go for signs of malicious behavior. GuardDog is backed by a publicly available threat dataset, giving developers and organizations real-time visibility into emerging supply chain risks.
This contribution directly supports OpenSSF’s mission to provide practical tools that harden open source ecosystems against common attack vectors—while promoting transparency and shared defense.
Datadog actively supports the open source security ecosystem through its engineering efforts, tooling contributions, and participation in the OpenSSF community:
These collaborations demonstrate Datadog’s investment in long-term, community-driven approaches to open source security.
Datadog takes the stage at OpenSSF Community Day North America on Thursday, June 26, 2025, in Denver, CO, co-located with Open Source Summit North America.
They’ll be presenting alongside Intel Labs in the session:
Talk Title: Harnessing In-toto Attestations for Security and Compliance With Next-gen Policies
Time: 3:10–3:30 PM MDT
Location: Bluebird Ballroom 3A
Speakers:
This session dives into the evolution of the in-toto Attestation Framework, spotlighting new policy standards that make it easier for consumers and auditors to derive meaningful insights from authenticated metadata—such as SBOMs and SLSA Build Provenance. Attendees will see how the latest policy framework bridges gaps in compatibility and usability with a flexible, real-world-ready approach to securing complex software supply chains.
Register now and connect with Datadog, Intel Labs, and fellow open source security leaders in Denver.
By contributing to secure development frameworks, creating open source tooling, and educating the broader community, Datadog exemplifies what it means to be an OpenSSF Premier Member. Their work is hands-on, standards-driven, and deeply collaborative—helping make open source safer for everyone.



Organization: Open Source Technology Improvement Fund, Inc. (OSTIF)
Contributor: Amir Montazery, Managing Director
Website: ostif.org
Critical open source software (OSS) projects—especially those that are long-standing and widely adopted—often lack the resources and systematic support needed to regularly review and improve their security posture. Many of these projects are maintained by small teams with limited bandwidth, making it challenging to conduct comprehensive security audits and implement best practices. The risk of undetected vulnerabilities in these projects presents a growing concern for the broader software ecosystem.
To address this gap, OSTIF leverages its OpenSSF membership to conduct rigorous security audits of critical OSS projects. Using a curated process rooted in industry best practices, OSTIF delivers structured security engagements that improve real-world outcomes for maintainers and users alike.
Through active participation in OpenSSF’s Securing Critical Projects working group and Alpha-Omega initiatives since their inception, and through strategic partnership with organizations like Eclipse Foundation, OSTIF receives targeted funding and support to carry out its mission. These collaborations help prioritize high-impact projects and streamline audit administration—despite the inherent complexity of managing funding approvals and coordination.
It’s pivotal that these important projects receive customized work. Each open source project is unique and so are its security needs, making standardization of audits difficult. OSTIF is able to invest time and expertise in scoping and organizing engagements to be tailored to the project’s best interests, necessities, and budget to generate effective investment in open source security.
OSTIF also incorporates other OpenSSF tools and services such as the OpenSSF Scorecard and the broader Securing Critical Projects Set, which complement its robust audit methodology and offer additional layers of insight into project health. In an ecosystem that is varied and complex, having security resources that can be applied to all projects contextually to generate impactful and sustainable security outcomes is incredibly valuable to all stakeholders, especially OSTIF.
OSTIF’s work has demonstrated the effectiveness of formal security audits in strengthening OSS project resilience. As a member of OpenSSF, OSTIF has been able to expand its reach, increase audit throughput, and reinforce the security practices of some of the open source community’s most essential projects. Since 2021, OSTIF has facilitated numerous engagements funded by OpenSSF. In March of 2025, OSTIF published the results of the audit of RSTUF with OpenSSF’s funding and support. Additionally, 2 more Alpha-Omega funded engagements will be published later this year.
“OSTIF is grateful for the support from OpenSSF, particularly for funding security audits both directly and via Project Alpha-Omega, to help improve the security of critical OSS projects.”
— Amir Montazery, Managing Director, OSTIF
In addition to the technical improvements achieved through audits, OSTIF’s OpenSSF membership has fostered valuable connections with project maintainers, security experts, and funders—creating a collaborative ecosystem dedicated to open source security. Building a community around security audits is a goal of OSTIFs; by sharing resources and providing a platform for researchers to present audit findings through meetups, their goal is to grow expertise and access to security knowledge of the average open source user.
To learn more about OSTIF’s work, visit their 2024 Annual Report. Visit their website at ostif.org or follow them on LinkedIn to stay up to date with audit releases.
