Intro Music (00:00)
Kevin Crosby (00:04)
I think that that was one of the most impressive things is just seeing these maintainers emerge out of a program and say, wow, you know, we live security now, you know, I think that that was pretty cool.
CRob (00:18)
Welcome to what’s in the sauce. The open SSF’s podcast where I talk to maintainers and developers, security researchers and experts all around the open source security ecosystem. It is my pleasure to be your host. My name is CRob. I’m the security architect for the open source security foundation and one of our co-hosts for this amazing little endeavor. And today I think we have a real treat. We have some people that have been deeply involved in upstream open source security for a very long time. And they have a pretty innovative idea that they’re going to be talking about this program we’re collaborating on together. So please let me welcome my friends, Kevin and Xavier from GitHub.
Kevin (01:04)
Thanks for having us today. It’s exciting to join the podcast and get to share this journey. And also very thankful for the partnership that you’ve brought through this program as well. Just quick background, Kevin here from GitHub. I lead our open source funding programs, specifically focused on things around GitHub sponsors that enable developers to get paid for their open source work. Think of things like hobbyists that are working on open source part-time to even full-time careers, or even folks that are starting to build companies around open source. And then programs beyond that through the secure open source fund as well as get up fund with with Microsoft’s venture fund as well
CRob (01:44)
and Xavier. Want to introduce yourself?
Xavier René-Corail (01:45)
Hey, Crob. Yes, I’m Xavier René-Corail from GitHub. I’m a Senior Director of Security Research and I lead the GitHub Security Lab. Our mission is to help secure open source. I’ve got a team of hackers who are doing security research. Another team who is in charge of creating the GitHub advisory database and managing our CNA. And, well, also, I’ve been with you, Crob, one of the…kind of initial members of the open source security foundation. We work together in the best practices working group and we are continuing to work together on securing open source.
CRob (02:26)
Yeah, I know Xavier, he and I used to be one of like 15 people that attended all the OG meetings five years ago when we got started off. I’m very glad to continue our partnership with this new evolution of kind of GitHub’s engagement with helping improve open source security.
Xavier René-Corail (02:34)
Haha right.
Xavier René-Corail (02:41)
Yes.
CRob (02:44)
So before we jump into the the SOS program, let’s talk a little bit and explore your open source origin stories. How did you get into open source and you cannot know why what drives you to keep participating here?
Kevin (02:57)
Xavier, you want to go first?
Xavier René-Corail (02:59)
Yeah, I can. So my first step in open source, let me check. So first of all, I started programming in the 80s. I think I started with Tron and I think, yes, my two first games were a snake and a pong. But then, after, you know, during high school, teenage years, I forgot a bit about that then got back to…to coding during college. And then after that, started my career as a developer. And then very quickly, I came into being in charge of development practices. And as part of that, I created the open source policy for the company I was in. And this is how I discovered open source by…um empowering the developers of my company to take advantage of open source and also of course to give back to open source and to contribute to open source. So this is how I came to work in open source.
CRob (04:11)
Awesome. What about you, Kevin?
Kevin (04:13)
Mine’s kind of an interesting story. So I’m non-technical background. Originally, I was in economics, almost did a PhD and freaked out right at the housing bust and decided to go into corporate finance. So a little bit different of an experience. But during that journey, I started working with some early stage startups and venture firms and they were building open source tools coming out of university labs and innovation. And so I got the first flavor through that and really understanding how do you leverage this technology to build innovative products, sometimes even companies around it. And then fast forward a couple of years when I was at Amazon, my next touch point was we were building products that leverage things like OpenFire and Hazelcast to build messaging applications.
One of the coolest things was because we were building with it, I wanted to make sure our engineering team was able to contribute back to that open source project. And so we were actually shipping alongside the community and making sure that they were getting some of the innovations, which was super, super cool to see. And then fast forwarding a little bit further is kind of staying within tech and venture. I was in the Alexa fund. We got to work with early stage startups investing in early stage open source AI companies got to evaluate and meet folks like Hugging Face, for example, and just kind of understanding where this ecosystem was going. And all that kind of brought this view of when I came to GitHub of how do you bolt on funding for open source, make it sustainable, drive innovation, and also create new pathways of funding for these maintainers through their journey. And so that’s what I came here to do. And it’s been super exciting over the past almost two years to think about how we can build new funding models for open source maintainers and projects. So excited for this new addition to that as well being kind of a next iteration of all of the career touch points I’ve had with open source.
CRob (06:10)
Totally didn’t arrange it, but that is an amazing transition. So let’s talk about GitHub Securing Open Source Software Fund. You know, why have you all decided to kind of organize and run this program?
Kevin (06:25)
Yeah, maybe kicking it off with an interesting insight that we had from the GitHub accelerator last year. One of the key modules that I was thinking about, and this was a brainstorm with Xavier, was do we actually know how much security education and training do people have for these emerging, fast growing projects? And even some of the ones that are becoming vital to the ecosystem.
And so I just literally threw it out to Xavier as an experiment. Like, can we try to run this content and engagement with these projects and see what the results would be? And so we did it. And maybe Xavier, if you want to talk about that initial experience, it’d be great to just kind of get your point of view from it as well.
Xavier René-Corail (07:08)
Yeah, well, it was exactly as you said, it was an experiment at first, right? And part of the accelerator and it came a bit last minute, right? But we, but I mean, at GitHub, we are ready to pivot fast and to try to think fast. And so we did some, we did some office hours, we did some one-on-one audits of this project and we did some basic training about security posture. And yes, and the results were great. mean, the engagement of the maintainers and the result, the impact that it had on them was great. So, so Kevin came again.
Kevin (07:58)
I came asking again, like, can we make this bigger? you know, I think the learning that we had is when you connect funding with time training and expertise, you’re able to maximize the impact of the training and education. so, and it also kind of dovetailed with a lot of the needs around security within the open source supply chain. So you kind of had this serendipitous moment of
high need, both in terms of like a macro level, but also high need from a developer level to make this work. And also lining that up with the incentive structure of funding and education that make it really special for these maintainers. so that actually is what kind of seeded this idea of let’s build a programmatic open source fund targeting security that links the funding to the outcomes of security specifically. And so we tested that hypothesis.
Honestly, I’ll say it took us, I think, 30 days round trip from like the seed to actually getting the program previewed at GitHub universe, bringing folks along, getting funders to commit to the program, lining up what a scaffolding curriculum might look like. And so we had that in like 27 days to preview it at GitHub universe. And I actually think that was the first time you and I spoke about it too, because we were like, hey, what do you think?
CRob (09:26)
Great, that was exactly.
Xavier René-Corail (09:27)
Yeah. I mean, it was great because so my team, the security lab, you know, we’re already doing these trainings, these free training, these additional content, this office hours. It was already part of what we do for open source. But with this program, we had the opportunity, you know, to have the, yeah, the programmatic power, know, and the marketing and the partnership and the funding, et cetera. So when Kevin came to me with that, said, yes, please, yes, let’s do that. And I must say that, yes, the turnaround was impressive. And in particular, thanks to partners like OpenSSF, who, I mean, CoreView, immediately said, yes, let’s do it. And yes, it went pretty fast indeed.
CRob (10:19)
So for our audience that may not be familiar, could you just broadly describe if a project is participating in the fund? How does that? What does that look like? What do they do?
Kevin (10:30)
Yeah, that’s a great question. Maybe I’ll tee this up really quickly by saying the overall architecture of the fund brings together funders, organizations, community partners like OpenSSF and some others that actually bring resource expertise and kind of shape the program and then GitHub as well as our maintainers. And so we kind of have this ecosystem surrounding this. And so what we’ve done as a program, as a maintainer that gets brought in,
You go through a standard application process, highlighting things around what your project is, what you do with your project, what your project does for the ecosystem, level of security awareness and education, the benefit of the funding specifically, what it can do to unlock resourcing, et cetera. And that’s kind of the process to bring them in. And once we’ve done that, we architected what I would consider a really unique structure. And I’m excited to talk about it for variety of reasons, but…
It’s effectively a three-week boot camp focused on security fundamentals, thinking about things that you need to have at day zero of building a project, all the way up to the lifespan of your project, thinking about implementing some of these techniques within the project itself, and then also some of the frontier stuff around AI. And so this three-week boot camp is around security fundamentals, best practices, but then we bolt on things like six months check-ins, 12 months check-ins.
community engagement with experts throughout the program to make sure that we actually line up all the resources that a maintainer would need, not just to learn it, but to actually embed it and embody it in their culture, make it scale out to their contributors, their communities, and even their consumers of their software. So I’m really excited about how the program’s been shaped. And a big kudos to Xavi, and I want him to talk about this in depth.
the security lab team is what bolts this together. And so I want to make sure like the impact of like how this all comes together is really focused on the security lab and the work they do. So Xavier, I would love you to kind of like jump in on the curriculum and education.
Xavier René-Corail (12:39)
Yeah, thank you, Kevin. Well, again, I mean, this is things that we were doing, but this program really brought the opportunity to amplify it. So it’s not only, it’s really together that we that we are, that we managed to put that up. So, so in terms of curriculum, yes, we, are trying during this free week bootcamp to, to, to, to have a mix of, you know, basic security posture and some advanced training on, for example, on fuzzing, on static analysis, things like that.
So you really have to mix because you have a mixed audience first. you need to, I mean, not everyone is at the same moment of their security journey, right? So you have to mix of that. We are trying to address all aspects from coding to incident response to vulnerability management.
So again, a mix of that. And of course, the important thing is that we are in continuous improvement mode. from the feedback from the first cohort, we will get to add more content. We have some people who are coming to us and proposing new content. And we’re like, yes, please come in.
So yeah, that’s in a nutshell, yes, that’s how we built this program. We are trying to get experts giving these training. So from us, but also from our partners, from the great David Wheeler, for example, from OpenSSF. So this is adding…
This is adding something to the learners, to maintainers, to have these great presenters who know what they’re talking about, giving them these presentations and answering the questions. So yes, that’s it.
Kevin (14:53)
I was gonna say, and just to double click on that a little bit, I mean, I think the uniqueness of it, to Xavier’s point, is how we framed and packaged it. So if we zoom out and say, what does a maintainer get? It’s three weeks security bootcamp with all of the education and expertise with these topics really focused on the programming. They get access to the security lab. They get access to the maintainer community.
They get access to the ecosystem partners that we’ve brought in and the funding partners as well. And then on top of that, they get embedded with like the data of like, how are we progressing in our own security journey? Like, we making progress? Are we embedding it in our community? How are we collaborating with other projects and maintainers through that as well? And so that’s kind of what the maintainers get. And the last thing that I think, you we didn’t really touch on, but the funding is really, you know, aligning the maintainers to spend the time commitment on it. So we provide a $10,000 stipend to the projects.
CRob (15:52)
Wow.
Kevin (15:52)
Most of that comes upfront, you know, the $6,000 upfront of the program to really solidify the three week boot camp. And then the others are to align onto the reporting and kind of the touch points and making sure they’re continuing on their security journey. so by aligning the funding and linking it to the outcomes that we’re trying to get with security, it becomes a really great model that is helpful for maintainers and for the projects that are being improved with security throughout the program.
CRob (16:20)
That’s awesome. So Xavier touched on it. We are just coming towards the end of the first cohort. Could maybe you share what’s been some of the most surprising things you’ve learned so far in interacting with both the funders and the maintainers and projects?
Kevin (16:41)
Maybe Xavier, do you want to go first?
Xavier René-Corail (16:44)
Well, yeah, my big surprise was the enthusiasm of everyone. I mean, I know this is something that is a passion for me, but I was, I mean, I don’t know, I wasn’t expecting that level of enthusiasm and of engagement from everyone. Really, you know, I was expecting some of the projects to be already quite advanced on the…you know, in their journey and then to be, to react a bit like, okay, there is content that is interesting for me, but some of the content is too basic. I was expecting that, right? No, everyone was really, really super engaged and super enthusiastic. So that was the big positive surprise for me. What about you, Kevin?
Kevin (17:41)
Yeah, I echo that. I kind of bucket them in three different functions. One is I think there was a very strong level of trust from the outset because they were all shared alignment on security within their project. And so I think everyone walked in and this kind of drove the enthusiasm of like, we’re all here for the same thing and having the same impact. So that was great. Two, I think the community lens was very fascinating to me just to see folks across different sizes of projects, stages of their growth or in kind of like distribution, as well as their own maturity journey within security, and like just seeing that community fuse really well together to cut across different frameworks, languages, et cetera, was really powerful. And I think the last thing that I’d say on this is the outcomes that we see is meaningful. Like not just from like, did the…things go red to green or anything like that, but really like you see them embody this change of what it means to be a steward of security with an open source. And that’s really unique. don’t think, and we kind of saw glimmers of that within the accelerator, but I didn’t think we’d, I didn’t know if we’d see it at this scope and scale. And I think that that was one of the most impressive things is just seeing these maintainers emerge out of a program and say, wow, you know, we live security now, you know, I think that that was pretty cool.
CRob (19:09)
Awesome. So on top of this, sounds like you’ve gotten a lot of great feedback. Is there anything that kind of stands out that you’ve got a maintainer or project kind of shared something really valuable to you all back from this experience?
Kevin (19:23)
I have a lot. I think one of the things that stands out in feedback is kind of going to the point of maturity curve is that it’s a very meaty subject. And so being able to scale content and education appropriately to meet maintainers where they are in their own journey is like one of the most critical things. And I think we’re we’re, you know, adjusting to that is like one one thing to think about. And then to Being able to touch upstream and downstream projects within their own Ecosystems is another area where I think that that’s a big opportunity for us to engage and kind of think about securing through the program as well. So those are just two immediate ones that I’m pretty excited about Xavi, what about you?
Xavier René-Corail (20:17)
Yeah, will double down on what you said Kevin: scaling to more projects, this will be the big challenge. And one other thing that I will add that I want to focus on also, because that was a positive feedback from participants, is adding some fun to the training. All of the training that were interactive and fun and with quizzes, et cetera. worked very well. so, yeah, you know, I used to say that boring is the arch enemy of learning. And so, yeah, I, I think that I want to add a bit more fun to the to the curriculum. So..
CRob (20:58)
I for one, totally agree with that. I think security is a lot of fun.
Xavier René-Corail (21:02)
It is.
Kevin (21:02)
The security is a lot of fun. You know, it was super interesting to see the modules I’d say that had interactive coding engagement. Like people really love just diving into it. And the other thing that was kind of unique that I don’t think it’s super surprising, but this concept of like see one, do one, teach one. Like it’s people coming through this journey and like, as you emerge, the first time you see it, like, my gosh, like this is overwhelming. The next time you do it, like I can actually do a coding exercise on this and actually implement some changes.
And then you see people a day later that are teaching like, this is how I did it, or this is how I’m thinking about it. It’s really cool to see that like, transpire throughout the program. And people loved it. Like to your point on fun, that made it fun, you know, to be able to teach people and engage is really unique.
CRob (21:50)
So let’s gaze out over the horizon, kind of what’s coming down the pipe for the GitHub Securing Open Source Software Fund. What do you have in your bag of tricks next?
Kevin (22:00)
Bag of tricks, that’s always a great question. As Xavier said, I mean, we have to scale. So we did the first session. Our objective is to do 125 projects this year. So we have multiple sessions that will be going on throughout the back half of the year. Session two will be kicking up in the next couple of months. And so we’re rapidly preparing for that. Yeah, I think that that’s where we’re looking forward to just in the back half of the year.
CRob (22:28)
Mm-hmm.
Xavier René-Corail (22:30)
Yeah. And in terms of curriculum, as I said, I’m receiving a lot of proposals to add content. going through that, going to add this content, I’m in particular interested if I have some ecosystem partners who are listening, I’m interested in language specific training for security. So if anyone has them, please reach out.
CRob (22:56)
Patches welcome, right?
Xavier René-Corail (22:58)
Yes, always.
CRob (23:00)
Nice. Well, let’s move on to the rapid fire part of our session. Are you ready for rapid, rapid, rapid fire? I have some wacky questions I’m going to ask you. Just give me the first thing that comes out of your on top of mind. First question and potentially controversial, VI or Emacs.
Xavier René-Corail (23:04)
Ha
Kevin (23:04)
Love it.
Xavier René-Corail (23:24)
Emacs.
Kevin (23:25)
I’m going to go the opposite just to say VI
CRob (23:29)
There are no wrong answers. Some are better than others, though. Also equally contentious, tabs or spaces.
Xavier René-Corail (23:30)
spaces.
Kevin (23:31)
I like tabs.
CRob (23:45)
You guys are balancing each other out very well.
Xavier René-Corail (23:45)
Right?
Kevin (23:45)
Yeah.
CRob (23:47)
Ice or neat?
Xavier René-Corail (23:50)
Neat.
Kevin (23:51)
Neat.
CRob (23:52)
excellent, excellent answer. Who’s your favorite open source mascot?
Xavier René-Corail (23:58)
Mona, of course.
Kevin (24:00)
Yeah, you can’t go wrong with Mona.
CRob (24:04)
That is perfectly fine. And finally, the most important question, mild or spicy food?
Kevin (24:12)
I’m all about spicy food.
Xavier René-Corail (24:12)
Spicy for me. Yeah, good, spicy. I’m from the Caribbean and yeah.
CRob (24:22)
Ohhhhhh….that’s spicy. Nice. Excellent. Well, thank you all for playing along. And as we wrap up, do you have any call to action or anything you want to ask our audience to potentially think about in regards to your program?
Kevin (24:33)
Certainly, I mean, right now, any maintainers that are interested in joining to up level their security, we’re welcoming applications. They’re rolling on going throughout the year. As you know, we have a robust pipeline of projects to go through in multiple sessions. So always feel free to apply. And then for funders, if they’re interested in helping secure their own dependencies, welcome those conversations. I think it allows us to unlock more opportunities and projects with with funders. They also bring unique insights and resources from their own ecosystems and Xavier said it too, and ecosystem partners that are ready for the journey to provide education, curriculum, engagement with maintainers. Some of them are even unlocking referrals for their maintainers that are coming through the program, things like that. So we would certainly welcome those opportunities throughout the year. It’s not just today, it’s not just tomorrow, but it’s an ongoing journey.
CRob (25:18)
Very nice.
CRob (25:27)
Xavi any advice for the audience to have or a call to action?
Xavier René-Corail (25:30)
No, honestly, nothing to add. I already made my cultivation. I need some language specific training for security. So if you want to help open source projects, please reach out to me.
CRob (25:48)
love it. Thank you gentlemen for helping shepherd this amazing project program together to help the ecosystem. And I really am excited to see the results as you are engaging directly with these maintainers. So thank you all for coming and I will wish everybody a happy open source and out there. Thanks all.
Xavier René-Corail (26:08)
Thank you, Crob.
Kevin (26:08)
Thanks for having us.
Outro (26:10)
Like what you’re hearing. Be sure to subscribe to What’s in the SOSS on Spotify, Apple Podcasts, antennapod, pocketcast or wherever you get your podcasts. There’s a lot going on with the OpenSSF and many ways to stay on top of it all. Check out the newsletter for open source news, upcoming events and other happenings. Go to openssf.org/newsletter to subscribe. Connect with us on LinkedIn for the most up-to-date OpenSSF news and insight and be a part of the OpenSSF community at openssf.org/getinvolved. Thanks for listening and we’ll talk to you next time on What’s in the SOSS.



 The recent Tech Talk, “
The recent Tech Talk, “




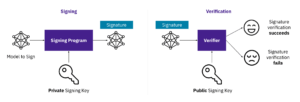
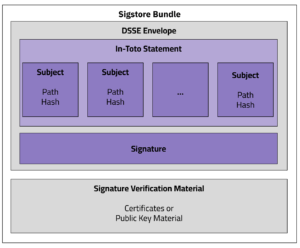
 Mihai Maruseac is a member of the Google Open Source Security Team (GOSST), working on Supply Chain Security for ML. He is a co-lead on a Secure AI Framework (SAIF) workstream from Google. Under OpenSSF, Mihai chairs the AI/ML working group and the model signing project. Mihai is also a GUAC maintainer. Before joining GOSST, Mihai created the TensorFlow Security team and prior to Google, he worked on adding Differential Privacy to Machine Learning algorithms. Mihai has a PhD in Differential Privacy from UMass Boston.
Mihai Maruseac is a member of the Google Open Source Security Team (GOSST), working on Supply Chain Security for ML. He is a co-lead on a Secure AI Framework (SAIF) workstream from Google. Under OpenSSF, Mihai chairs the AI/ML working group and the model signing project. Mihai is also a GUAC maintainer. Before joining GOSST, Mihai created the TensorFlow Security team and prior to Google, he worked on adding Differential Privacy to Machine Learning algorithms. Mihai has a PhD in Differential Privacy from UMass Boston.
 Daniel Major is a Distinguished Security Architect at NVIDIA, where he provides security leadership in areas such as code signing, device PKI, ML deployments and mobile operating systems. Previously, as Principal Security Architect at BlackBerry, he played a key role in leading the mobile phone division’s transition from BlackBerry 10 OS to Android. When not working, Daniel can be found planning his next travel adventure.
Daniel Major is a Distinguished Security Architect at NVIDIA, where he provides security leadership in areas such as code signing, device PKI, ML deployments and mobile operating systems. Previously, as Principal Security Architect at BlackBerry, he played a key role in leading the mobile phone division’s transition from BlackBerry 10 OS to Android. When not working, Daniel can be found planning his next travel adventure.









