
By Edoardo Dusi
DruBOM is a Software Bill of Materials (SBOM) for Drupal. It is a list of all the dependencies of a Drupal project, including the Drupal core, modules, themes, and libraries.
Securing the software supply chain is a hot topic for organizations globally. The recent SolarWinds hack demonstrated that even the most security-conscious organizations can be vulnerable to supply chain attacks, and as a result, government agencies and security experts worldwide agreed on the need for standards and best practices to achieve a more secure software ecosystem.
One fundamental element is the ability to identify all components of a software project, including dependencies, and their versions. This is called a Software Bill of Materials (SBOM). With this information, organizations can track the components and their versions, and be able to identify and mitigate vulnerabilities.
There are several initiatives to create standard formats for SBOMs, including CycloneDX, SPDX, and others.
Open source software security is an ecosystem-wide effort. While DruBOM is not an OpenSSF Technical Initiative, DruBOM is part of the php/Drupal world, a huge part of the open source ecosystem. DruBOM leverages tools like Syft and Grype, which are often cited by OpenSSF Technical Initiatives, along with the SBOM standards.
We are working on a Drupal-specific SBOM called DruBOM. In this post, we will share with the broader open source software security community what DruBOM is, how it works, and how you might use it for your open source software security use cases.
SBOMs in the CI/CD
Automated SBOM generation fits seamlessly into the CI/CD process, improving the efficiency and security of software development workflows. By integrating SBOM tools into the CI/CD pipeline, organizations can ensure that each new application build or package is automatically followed by a list of its components and dependencies, along with their versions.
This automation maintains consistency across iterations of a software product and ensures that all stakeholders have access to the most current version of the SBOM. Automated SBOMs also simplify the process of detecting vulnerabilities and managing licensing issues, as they can be fed into tools that scan for known vulnerabilities in dependencies and verify compliance with licensing requirements.
The quality of an SBOM can also be automatically measured by defining a set of minimum data fields that must be present using two open source tools, one is the NTIA Conformance Checker from SPDX, which checks if the file contains the minimum elements to ensures basic functionality such as vulnerability management, and eBay’s SBOM Scorecard, which determines if an SBOM conforms to the specification and includes package IDs, package versions, and licenses.
What is DruBOM?
First of all, this is a Drupal module, it needs to be downloaded and installed using Composer, and requires Drupal 9.3 and above or Drupal 10.3 and above.
To generate the SBOM it integrates Anchore Syft, so this needs to be installed on the server. Syft is a CLI tool written in Go that analyzes the contents of a container image or directory on the file system and generates an SBOM in various formats, including CycloneDX and SPDX.
If these requirements are met, DruBOM will generate an SBOM for the Drupal project, including the Drupal core, modules, themes and libraries, as well as PHP and JavaScript dependencies. The default format is CycloneDX, but it can be configured to use other formats supported by Syft.
How Does DruBOM Work?
The initial version of the module is very simple. It detects the Syft binary and calls it, passing the Drupal root directory and the output format as parameters, then saves the output to the key-value store with the drubom.sbom key and the current timestamp.
You can then download the SBOM, or better yet, use it with automated tools to detect vulnerabilities and/or licensing issues.
How to Use DruBOM?
The first step is to add the DruBOM module to your Drupal project.
Run composer require sparkfabrik/drubom and then enable the module with drush or via the Drupal administration interface.
After installing and enabling the module, navigate to Administration » Configuration » System » DruBOM settings and specify the path of the Syft binary. The binary must be executable by the PHP process.
Note: the PHP configuration must allow the use of proc_open(), which is equivalent to exec() in terms of security.
Once the configuration is saved, generate the SBOM by clicking the Generate SBOM button on the settings page or by visiting the /drubom/generate path with a user who has the necessary permissions. The generated list will be saved on the Drupal DB and can be downloaded by clicking the Download SBOM button.
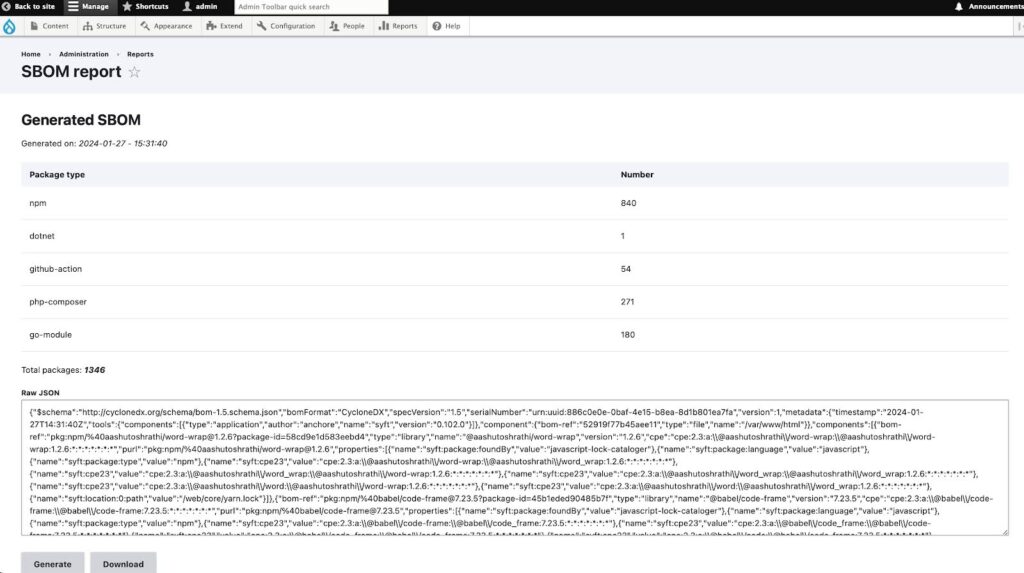 Image: Screenshot of a DruBOM administration page
Image: Screenshot of a DruBOM administration page
You can also use the drush drubom:generate command to generate the SBOM from the command line. To download it, use the drush drubom:download command.
How to Distribute DruBOM?
Once generated, the SBOM should be included in the release package and automatically updated with each build.
It is important to clearly document how to access and use the SBOM within your project’s documentation. If your Drupal website package is hosted on a platform like GitHub or GitLab, consider adding the SBOM to the repository or linking to it from the README file. This will ensure that users and developers can easily find and understand its contents.
The main idea is to automatically generate the SBOM as part of the CI/CD process, update it with every build, and distribute it along with your project’s package to ensure the security and compliance of a software supply chain.
What’s Next?
The scope of the module is very specific, so we don’t expect it to grow much in terms of features. During the Drupal Contribution Weekend 2024 we improved the documentation and the administration interface, added an integration with the System Status page in Drupal administration, and started integrating with Grype to also detect vulnerabilities, which is a step forward in terms of security.
We consider this module to be fully stable and ready for production use, so we encourage you to try it out and give us feedback. If you find any problems, please report them to the issue queue.
About the Author
 Edoardo is a Developer Relations Engineer at SparkFabrik, a company that helps organisations build digital products with open source technologies. He has a strong software developer and team leader background, working on various projects and platforms. He is passionate about creating and sharing content that educates and inspires other developers, such as tech talks, videos, podcasts, conferences, and more. He enjoys connecting with the developer community and promoting the benefits of open source software.
Edoardo is a Developer Relations Engineer at SparkFabrik, a company that helps organisations build digital products with open source technologies. He has a strong software developer and team leader background, working on various projects and platforms. He is passionate about creating and sharing content that educates and inspires other developers, such as tech talks, videos, podcasts, conferences, and more. He enjoys connecting with the developer community and promoting the benefits of open source software.