
By Michael Lieberman, Kusari and Brandon Lum, Google
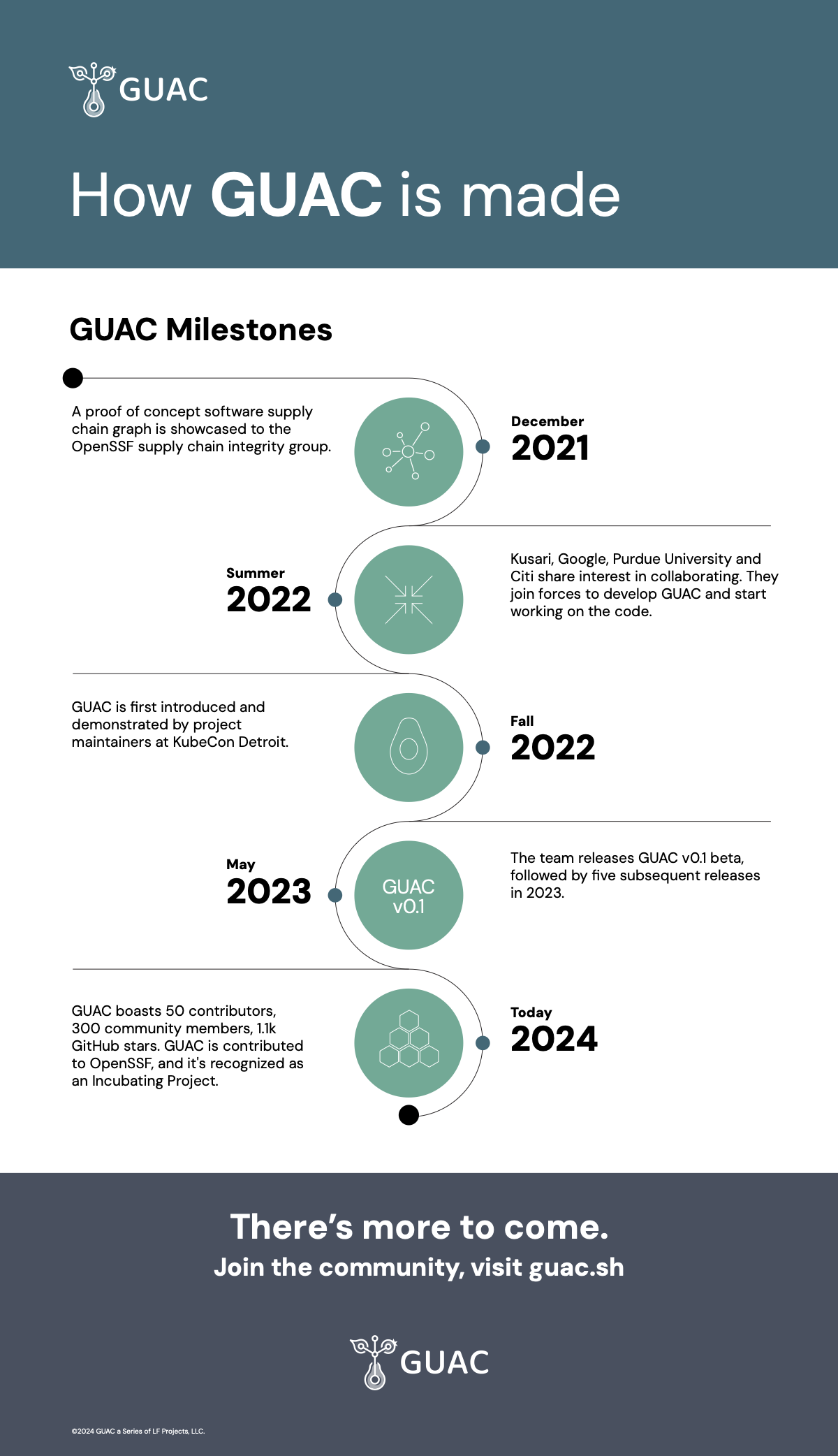
The Graph for Understanding Artifact Composition (GUAC) maintainers are pleased to announce the project has joined the Open Source Security Foundation (OpenSSF) as an Incubating Project. GUAC is an open source supply chain security project that provides dependency management and actionable insights into the security of software supply chains. GUAC was created by Kusari, Google, and Purdue University, and is supported by industry-leading financial services and technology companies, including Yahoo!, Microsoft, Red Hat, Guidewire, and ClearAlpha Technologies.
GUAC Enables Developers and Security Teams
The frequency of software attacks and increased use of open source tooling has created a significant lack of confidence in the integrity and security of the software supply chain. GUAC responds to the problem by being the source of truth for what’s going on in your software. GUAC can help to eliminate the information gap between developers and security teams, providing a shared understanding of software knowledge gaps, compliance and threat detection.
Since the beta release last May, GUAC has been establishing itself as the tool for knowing your software supply chain. The project has 50 contributors, 300 community members and more than 1,100 GitHub stars.
About GUAC
GUAC looks across all first party, third party and open source software, aggregating the software security metadata into a high fidelity graph database to locate, store, analyze and correlate software artifact data. With GUAC, users can establish connections and compliance in their software catalog, unveil gaps in software supply chain data, and enable threat detection and response. The tool ingests and analyzes software supply chain metadata from a myriad of internal and external sources and multiple common metadata document types, including:
- Taking in Software Bill of Materials (SBOMs) in both SPDX and CycloneDX formats and transforming them into data nodes and relationships, providing insights into software and dependencies
- Ingesting and transforming SLSA and in-toto attestations into their constituent facts, offering crucial information about the provenance and integrity of software components
- Being flexible and extensible to ingest data from local file systems, AWS S3, Google Cloud, and external package repositories like GitHub Releases
- Embracing additional metadata from sources like the deps.dev and OSV APIs.
-
GUAC Use Cases
GUAC provides seamless visibility across an organization’s software ecosystem, easily integrating with existing tools. It also is an effective tool for managing third-party risk and incident response. GUAC supports users to:
Establish connections and compliance
Detect and respond to threats | Determine ownership of applications by organization | Look for evidence that apps meet organizational policy | Determine which application is missing SBOM or SLSA attestations | Conduct SBOM Diffs to quickly determine changes between versions
“The value we see with GUAC is its flexibility and plugin architecture leading up to helping the users achieve compliance at different levels.” – Anoop Gopalakrishnan, VP of Engineering, Guidewire Software
Unveil gaps
Identify the most used critical components in a software supply chain ecosystem | Track if all binaries in production trace back to a securely managed repository | Find exposures to risky dependencies to prevent compromises before they happen

“GUAC allows us to ingest a large number of SBOMs and also provides an interface to visualize the current state of images & packages used at Yahoo in real time.” – Hemil Kadakia, Sr. Mgr. Software Dev Engineering, Paranoids, Yahoo
Detect and respond to threats
Indicate the blast radius of a bad package or vulnerability and provide information and a patch plan towards remediation | Track a suspicious event back to when it was introduced

“GUAC’s ability to trace risks back to their source aligns with our proactive risk awareness goals, enabling companies to spot and tackle potential issues early on.”– Sean Terretta, CTO, ClearAlpha
Why OpenSSF is the Right Home for GUAC
As core contributors, Kusari, Google, and Purdue University, we are thrilled to continue the work within OpenSSF. Being part of OpenSSF, the premier open source foundation for securing open source and the software supply chain, will strengthen GUAC. Open SSF provides access to a variety of programs and services to support GUAC, including:
- Domain experts in areas such as SBOMs and VEX to enable GUAC with cutting edge functionality
- Multiple software supply chain groups and programs to work with and have obtain critical input data for GUAC, such as SLSA, VEX, OSV, deps.dev, Scorecard
- End user validation of GUAC’s value and feedback on improvements to further resolve DevSecOps friction
Get involved with the GUAC project
We want to help more end users get onboarded to GUAC and speak with people struggling to get visibility into their supply chain issues. The community is seeking support for:
- New integrations of data sources and feeds via collectors and certifiers
- New use cases that can be fulfilled via GUAC’s built-in graphQL API or REST API
- End user testing and feedback on new features / requirements
If you want a friendly and open space to ask questions and learn about SBOMs, SLSA, S2C2F, OpenVEX, third party risk and other open source software supply chain topics, then the GUAC community is a great first step. To connect with us, visit https://guac.sh/community/ where you can join the GUAC slack channel on the OpenSSF Slack, engage in monthly community calls every 3rd Thursday at 10am Pacific, participate in office hours, and add yourself to the public mailing list. GUAC maintainers will be at KubeCon EU in Paris, so don’t hesitate to approach us and grab some swag.
About the Authors

Brandon Lum loves designing and implementing computer systems (with a focus on Security, Operating Systems, and Distributed/Parallel Systems). Brandon is Co-chair Emeritus of the CNCF Security TAG, and as a part of Google’s Open Source Security Team, he works on improving the security of the Open Source ecosystem. Previously at IBM Research, Brandon worked on various security areas such as: container content protection via encryption and image signing, identity, and kernel attack surface reduction.

Michael Lieberman is Co-Founder and CTO of Kusari, a software supply chain security startup. Michael haspreviously worked in the financial industry, architecting cloud migrations with a focus on security. In addition, he is an OpenSSF Governing Board and TAC member; a member of the SLSA steering committee, an emerging supply chain security standard; as well as a CNCF Security TAG lead.