
By Luke Hinds, Stacklok and Hayden Blauzvern, Google’s Open Source Security Team
This month’s spotlight focuses on the Sigstore project. Digital signatures play a critical role in the software supply chain, by providing verifiable attributes of authentication, integrity, and non-repudiation of artifacts as they are distributed between consumers and producers. By ensuring that the origin of the software can be reliably traced back to its source, digital signatures also help establish a chain of trust, confirming that the software is from the claimed source. This is particularly crucial for build provenance, as it allows users to verify not just the integrity of the final artifact, but also the integrity of the entire build process, ensuring that the software was compiled and packaged within a specific environment.
Historically, the adoption of digital signatures within open source software ecosystems has been impeded by significant complexity, poor user experience, and scalability challenges in binding key material to digital identities. Digital signature schemes require signers to manage both the distribution of public key material to verifiers and protection of private key material to avoid compromise.
Sigstore was founded to address the fundamental challenges preventing wide scale usage of digital signatures within the software supply chain. Sigstore is a set of open source projects and services that dramatically simplify the creation and verification of digital signatures. It achieves this through a modular architecture that integrates proven technology solutions from adjacent domains (including Certificate Transparency, OpenID Connect, and Workload Identity among others) while reusing industry standard cryptographic algorithms and best practices. Sigstore removes the need for managing signing keys, defaulting to the use of identity-bound ephemeral signing certificates, while making signing events transparent and auditable.
Highlights of the Past Few Months
Here is what we’ve accomplished over the past few months:
- Sigstore general availability (GA) of public-good services in Oct 2022, where we have maintained a 99.5% availability SLO via a multi-vendor 24/7 oncall rotation
- A few usage stats: 46 million signatures logged post-GA, 22,000 unique GitHub projects using Sigstore to sign artifacts and attestations
- Sigstore support in npm launched both in public beta in April and GA in October, enabling Sigstore-signed SLSA attestations linking source with binary artifacts
We also recently published a multi-year roadmap that outlines Sigstore’s strategy for adoption with open source ecosystems and package managers and a technical roadmap for Sigstore’s clients and services. Sigstore is becoming the de facto standard for both signing and verification of OSS software artifacts and metadata.
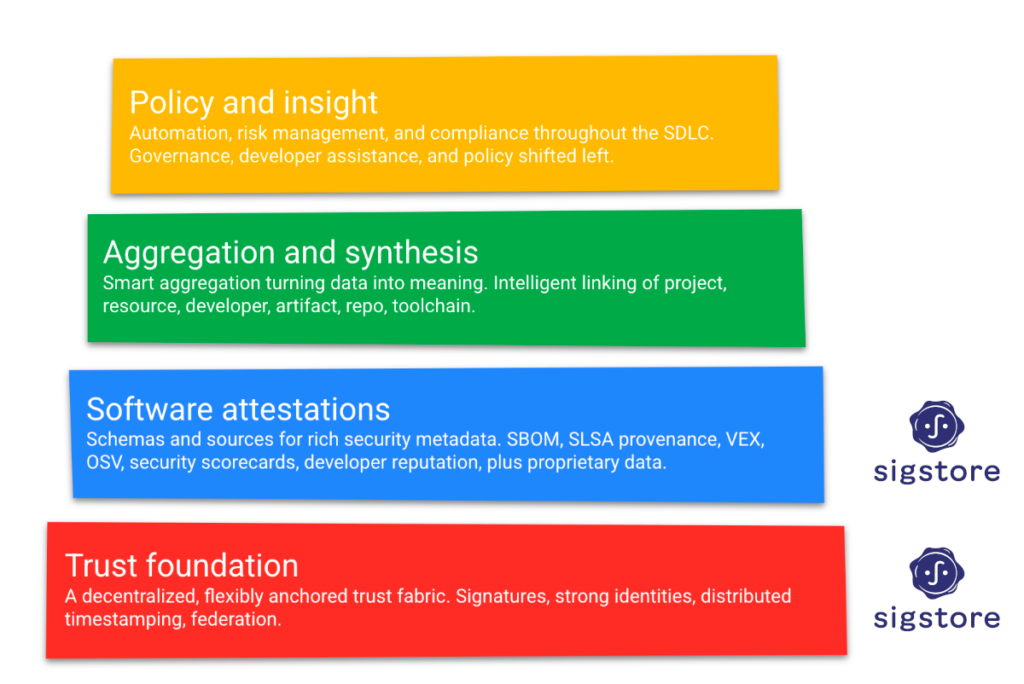
Image 1: Sigstore provides a trust foundation for supply chain security, including many OpenSSF projects.
New and Upcoming Initiatives
- Focus on OSS package managers as the primary path for Sigstore adoption in the OSS ecosystems: For example, Homebrew recently began adopting Sigstore, and integrations with PyPI (Python) and Maven (Java) are also underway. If you maintain a package manager, please reach out if you are interested in adopting Sigstore and/or SLSA!
- Making Sigstore infrastructure services simpler to operate for both public and private operators: This will simplify deployments for private companies who want to secure their software deployments without needing to rely on the public infrastructure.
- Collaborating with the academic community to provide stronger trust assurances and privacy guarantees: We are looking to explore innovative ways of doing this such as post-quantum signing and privacy-preserving constructions of identities. We’d also like to make it easier to operate log monitors so that signers can verify when their identity is used to sign an artifact.
- Ensuring that verification is as seamless as signing: Sigstore has greatly simplified signing, but now these signatures need to be verified through the software development lifecycle. We will leverage tools like Policy Controller to build out this capability.
Get Involved
If you’re interested in learning more about Sigstore, check out our website and documentation.
If you’re interested in discussing or integrating with Sigstore, we have an active community on Slack (invite link). We also encourage filing issues or starting discussions on GitHub.
Check out our community calendar where all recurring and one-off community meetings are shared. We have a bi-weekly community meeting every other Tuesday at 9:30am PST, accessible from the linked calendar. Recordings for all meetings are available on our YouTube channel.
If you’d like to make technical contributions to Sigstore, check out repositories in our GitHub organization. Many repositories include tags on open issues that are good starter issues. Cosign, Rekor, and Fulcio are some of Sigstore’s larger repositories written in Golang, and we also have Sigstore clients written in Python, JavaScript, Java and Rust.
About the Authors
 Luke Hinds is the CTO of Stacklok, Inc., a company focused on solving secure supply chain issues within open source. Luke started the Sigstore project in 2020 and currently serves as the chair of the Technical Steering Committee.
Luke Hinds is the CTO of Stacklok, Inc., a company focused on solving secure supply chain issues within open source. Luke started the Sigstore project in 2020 and currently serves as the chair of the Technical Steering Committee.
 Hayden Blauzvern is a technical lead manager on Google’s Open Source Security Team, focused on making open-source software more secure through code signing and applied transparency. Hayden is a maintainer and the community chair on the Sigstore project.
Hayden Blauzvern is a technical lead manager on Google’s Open Source Security Team, focused on making open-source software more secure through code signing and applied transparency. Hayden is a maintainer and the community chair on the Sigstore project.