
By Jay White, Microsoft and David A. Wheeler, Linux Foundation
A robust strategy around securing how developers consume and manage open source software (OSS) dependencies when building software is essential. The Secure Supply Chain Consumption Framework (S2C2F) is a consumption-focused framework that uses a threat-based, risk-reduction approach to mitigate real world threats in Open Source Software (OSS). Today, we are pleased to announce that it has been adopted by the OpenSSF under the Supply Chain Integrity Working Group and formed into its own Special Interest Group (SIG). The Secure Supply Chain Consumption Framework (S2C2F), when coupled with a producer-focused artifact-oriented framework such as Supply chain Levels for Software Artifacts (SLSA), gives software producers and consumers a complete guide for how to approach building and consuming software securely.
What is the Secure Supply Chain Consumption Framework (S2C2F)?
The S2C2F was built and donated by Microsoft, where it has been used and refined internally since 2019. It was built as a consumption-focused framework that uses a threat-based, risk-reduction approach to mitigate real world threats. The framework enumerates a list of real-world supply chain threats to OSS and explains how the framework’s requirements mitigate those threats. It also includes a high-level platform- and software-agnostic set of focuses that are divided into 8 different areas of practice:
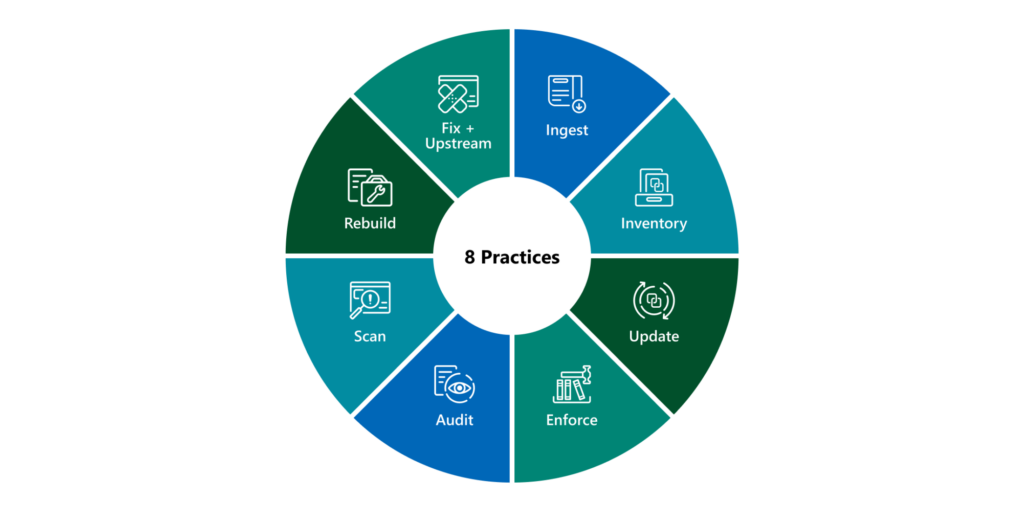
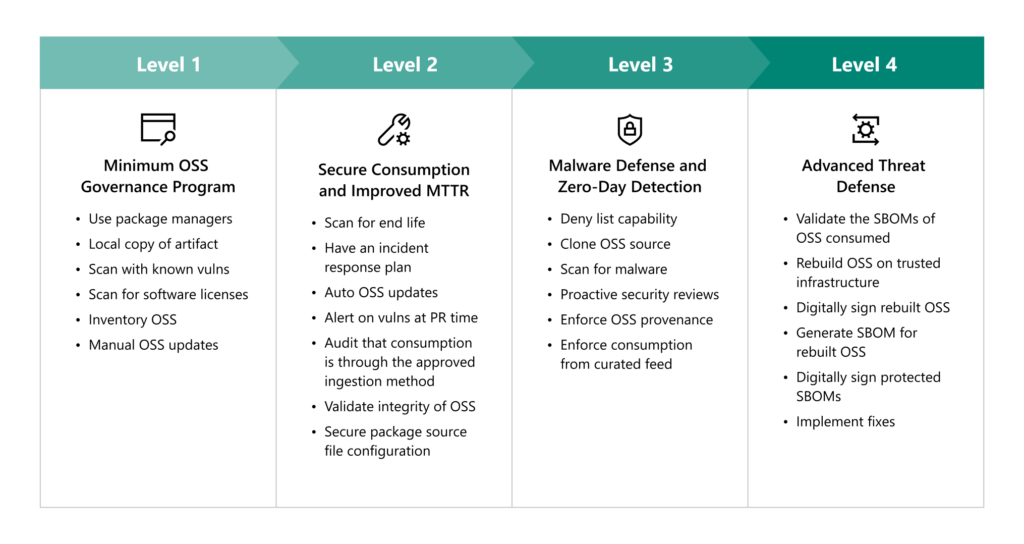
Each of the 8 practices comprises requirements to address the threats and reduce risk. The requirements are organized into 4 levels of maturity. Each maturity level has a theme represented in Levels (1-4).
- Level 1 – represents a basic set of governance practices already applied by many organizations, such as using package managers (to automate tracking and updating of reused components), inventorying your OSS, scanning for known vulnerabilities, and updating OSS dependencies.
- Level 2 – builds upon Level 1 by leveraging technology that helps improve your Mean Time to Remediate (MTTR) vulnerabilities, with the goal of fixing faster than the adversary attacks.
- Level 3 – is focused on proactive security analysis combined with preventative controls that mitigate against accidental consumption of compromised or malicious OSS, problems that are much less common but can be harmful if they occur.
- Level 4 – represents controls that mitigate against the most sophisticated attacks but are also the most difficult to implement at scale; therefore, level 4 should be considered aspirational in many situations and reserved for your dependencies in your most critical projects.
“We have seen massive success with both internal and external projects who have adopted this framework,” said Mark Russinovich, the Azure CTO. “Using the S2C2F, teams and organizations are able to more efficiently prioritize their efforts in accordance with the maturity model. The ability to target a specific level of compliance within the framework means teams can make intentional and incremental progress toward reducing their supply chain risk.”
The S2C2F includes a guide to assess your organization’s maturity, and an implementation guide that recommends tools from across the industry to help meet the framework requirements for any company.
One of its primary strengths, and why we were so excited to adopt it into the OpenSSF, is how well it pairs with any producer-focused framework such as SLSA. For example, S2C2F’s Level 3 requirement for provenance of all dependency artifacts can be achieved through generated artifact provenance in such a manner deemed trustworthy through SLSA.
OpenSSF is committed to providing pragmatic and accessible frameworks to help secure software supply chains
According to Sonatype’s 2022 State of the Software Supply Chain Report, supply chain attacks specifically targeting OSS have increased 742% annually over the past 3 years. In addition, 95.5% of known-vulnerable downloads had a non-vulnerable option available. The S2C2F is designed from the ground up to protect developers from accidentally consuming vulnerable packages (including malicious and compromised packages), helping to mitigate supply chain attacks through decreasing consumption-based attack surfaces. As new threats emerge, the OpenSSF S2C2F SIG under the Supply Chain Integrity Working Group is committed to reviewing and maintaining the set of S2C2F requirements to address them.
View or download the guide now to see how you can improve the security of your OSS consumption practices in your team or organization. S2C2F is in the process of refinement; to participate, come join the S2C2F community discussion within the OpenSSF Supply Chain Integrity working group. We are excited to get feedback and contributions to S2C2F, see organizations benefit from its adoption, and deliver on our vision for supply chain security end to end.