
By Jonathan Meadows
In today’s digital landscape, the software supply chain security topic has certainly caught on in the mainstream with a surge of blogs, conference talks, presentations and startups actively engaged to help address this critical threat. We are also starting to see various frameworks and standards emerge to address this multifaceted puzzle as the number of supply chain attacks increase.
From a “software consumer perspective”, how do we know where to start to address the real supply chain threats? Which risks are more critical than others? What framework or standard should be adopted quickly? Those were the questions posed in the OpenSSF End Users Working Group where engineers got together to figure out how to secure enterprises and consumers who leverage software. We now have an initial threat model that applies to the typical enterprise open source software consumer with common software assets and would like to invite you to participate in developing the next iteration.
Threat Modeling Approach
It turns out software supply chain security is a complicated problem. One approach to identifying where to start is to threat model the system under attack to understand where the weaknesses are, then get a view of their prevalence. That last part is important. Whilst there are many threats and areas to fix in the supply chain space, not all of them are created equal. By leveraging the threat model and data showing known attacks, we can see where an end user could focus to secure their supply chain. Additionally, ecosystem-wide it allows us to identify where the many great frameworks such as SLSA or S2C2F fit in or if there are any gaps in the capabilities available. Threat modeling would then lead to a prioritization of where to focus and any gaps that need to be addressed.
End Users Working Group
With this approach in mind, the End Users Working Group began collaborating on an effort to model a typical software consumer in order to identify these threats. This is a high-level threat model aimed to be instructive rather than exhaustive as enterprises are of multiple different sizes and maturity. The initial material that seeded this effort came from work I put together at Citi detailing an early enterprise threat model and work from Henrik Plate from Endor Labs who co-authored several seminal papers on open source supply chain security, e.g., Backstabber’s Knife Collection and Taxonomy of Attacks on Open-Source Software Supply Chains.
Initial Threat Model
Thanks to the work from the End Users Working Group, we now have an initial threat model. Starting with a very high-level depiction of a typical enterprise open source software consumer with common software assets. This model then details high-level threats against each component. Many of these threats should resonate as they have been actively attacked and reported in the media.
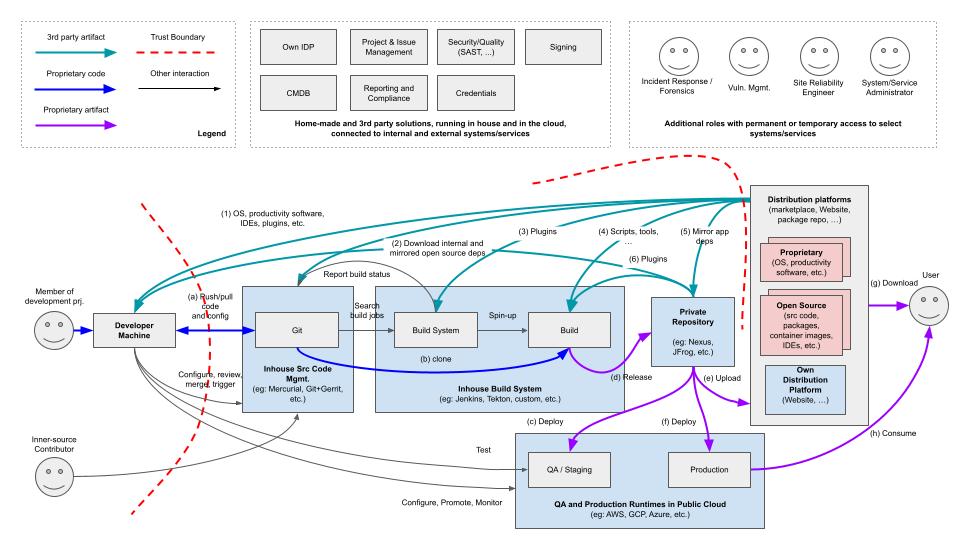
Architecture diagram of a large in-house development organization
Our next step is to continue digging deeper into these threats to flesh out the pertinent issues and finally map the existing frameworks on this architecture to identify the potential gaps or priorities that need to be followed.
Get Involved
We are continuing to build out this model in the End Users Working Group and would welcome anyone interested in joining us. The group is focused on building out the models and many are doing this as part of their day jobs too, which brings a practical perspective. The team gets together weekly at 9:30 am PST on Monday and bi-weekly as part of the End Users Working Group call on Thursday at 7:00 am PST. There are lots of ways to get involved and contribute. Even if you are new to threat modeling, come along to one of the meetings and get involved.
Getting involved is a great opportunity to work with other practitioners and to get some guidance on how to perform a threat model. We’re a friendly bunch and are focused on making a difference, so come along and contribute!
About the Author
 Jonathan Meadows is the chair of the Open Source Security Foundation (OpenSSF) End Users Working Group. He is also a Citi Tech Fellow and the Head of Cloud, Application and Software Supply Chain Security at Citi. He is a keen advocate of DevSecOps, Open Source, codified security controls and automated security testing. Jon started the CNCF Financial Services and supply chain working groups where he co-authored the CNCF Supply Chain Best Practices white paper. He actively contributes to the community as a board member for the OpenSSF and chair of the OpenSSF End Users Working Group.
Jonathan Meadows is the chair of the Open Source Security Foundation (OpenSSF) End Users Working Group. He is also a Citi Tech Fellow and the Head of Cloud, Application and Software Supply Chain Security at Citi. He is a keen advocate of DevSecOps, Open Source, codified security controls and automated security testing. Jon started the CNCF Financial Services and supply chain working groups where he co-authored the CNCF Supply Chain Best Practices white paper. He actively contributes to the community as a board member for the OpenSSF and chair of the OpenSSF End Users Working Group.