
From August 25 to 28, 2025, the Linux Foundation hosted a high-impact week of open source collaboration and innovation in Amsterdam. OpenSSF’s participation, in both Open Source Summit Europe and OpenSSF Community Day Europe, brought together developers, maintainers, researchers, and policymakers to strengthen software supply chain security and align on global regulations like the EU Cyber Resilience Act (CRA). Photos and recordings are now available!
Highlights from Open Source Summit Europe
The OpenSSF booth at Open Source Summit drew strong engagement. Many attendees were excited to discover that the tools they already use, such as sigstore, SLSA, and OpenSSF Scorecard, are part of the broader OpenSSF ecosystem. Thank you to everyone who stopped by and engaged with our projects. Whether you’re already leveraging OpenSSF projects and tools, just starting to explore them, or looking to stay involved, we’re glad to have you with us.
The summit featured timely sessions focused on compliance, transparency, and cross-sector coordination.
“Zephyr: Evolving to CRA Readiness” — Kate Stewart (Linux Foundation) explored how Zephyr is aligning with CRA requirements, emphasizing automation, SBOMs, and long-term support strategies. She shared how The Zephyr Project is helping product makers prepare for the Cyber Resilience Act, from automated SBOMs to five-year LTS vulnerability fixes.
“Trust, but Verify: Proactive Security in Open Source” — Eve Martin-Jones (Google) delivered a timely talk on tackling the gap between source code and built artifacts, especially relevant in the wake of recent high-profile attacks like xz and boltdb-go.
“Chain Reaction: Remixing CNCF’s Supply Chain Security Guide for 2025” — John Kjell (ControlPlane) presented updated approaches for securing open source supply chains. He highlighted the interconnected nature of software supply chains and the cascading effects of security failures, showcasing how OpenSSF projects like SLSA, GUAC, bomctl, and sigstore are linking up defenses.
Panel: Prepare for the CRA: Open Source Governance in the Age of Cyber Resilience — Andrew Martin (ControlPlane), Eddie Knight (Sonatype), Megan Knight (Arm), and Michael Lieberman (Kusari) explored how roles like maintainers, stewards, manufacturers, and distributors must evolve under the CRA. The panel spotlighted the OpenSSF Global Cyber Policy Working Group and how OSPS Baseline supports these shifts.
“Linux Foundation Initiatives Supporting the Implementation of the EU Cyber Resilience Act” — Mirko Boehm (Linux Foundation Europe), Hilary Carter (Linux Foundation Research), and Christopher “CRob” Robinson (OpenSSF) provided a strategic overview of how the Linux Foundation and OpenSSF are advancing CRA readiness. This includes contributions to the EC CRA Expert Group and education programs such as LFEL1001.
“Your SBOM Is Lying to You – Let’s Make It Honest” — Justin Cappos (New York University) & John Kjell (ControlPlane) made a compelling case for verifying and improving SBOM accuracy to build real trust in software artifacts.
Highlights from OpenSSF Community Day Europe (August 28, 2025)
This full-day deep dive into open source security showcased the OpenSSF community’s leadership and ongoing progress.
Opening Remarks from Adrianne Marcum (OpenSSF) set the tone. We celebrated key milestones in public sector engagement, the DARPA AIxCC Challenge, the intersection of AI and security, and the launch of Model Signing v1.0. We also announced the Golden Egg Award winners: Ben Cotton (Kusari), Kairo Araujo (Eclipse Foundation), Katherine Druckman, Eddie Knight (Sonatype), and Georg Kunz (Ericsson). The Golden Egg Awards recognized five outstanding community contributors whose efforts have helped advance open source security practices, their contributions continue to shape and strengthen the ecosystem.
Keynote: Bridging Policy and Communities – OpenSSF Involvement in EU Cyber Policy — Madalin Neag (EU Policy Advisor, OpenSSF) emphasized the need for cross-border cooperation in cybersecurity. He outlined how OpenSSF is working globally to shape inclusive legislation, equip developers with the right tools and knowledge, and build frameworks that anticipate emerging threats.
Keynote: Improving Security Data With ORBIT — Ben Cotton (Kusari) and Eddie Knight (Sonatype) introduced how the ORBIT Working Group is defining and communicating critical security data. They discussed the OSPS Baseline, Gemara, Security Insights, and supporting tools such as Minder and OpenSSF Scorecard.
Keynote: From Gatekeepers to Partners: How Developer Relations Transforms Security Tool Adoption — Katherine Druckman highlighted how developer relations can drive meaningful security outcomes. Her session focused on enabling developers through context, partnership, and clear feedback loops.
Becoming a Good CRA Citizen: A Baseline Guide for Open Source Projects — Adolfo García Veytia presented how projects can align with CRA requirements using the OSPS Baseline, improving transparency through SBOMs, VEX documents, and attestations.
Securing RSTUF To Secure Your Supply Chain – Helen Woeste, Kairo De Araujo & Eric Sesterhenn (OSTIF) presented how architecture and security design decisions in RSTUF impact the security posture of the entire project. Their talk highlighted how collaborative work between funders, maintainers, and security auditors helped improve and verify RSTUF’s effectiveness as a key component in securing software supply chains.
GUAC+Trustify: Building a Common Supply Chain Knowledge Graph — Ben Cotton (Kusari) and Dejan Bosanac (Red Hat) showcased how integrating efforts by GUAC and Trustify creates a more comprehensive and interoperable ecosystem for supply chain metadata.
OpenSSF Bug Squashing Allies — Georg Kunz and Jan Melen (Ericsson) shared how community collaboration can accelerate vulnerability remediation, coordinate with upstream projects, and enhance trust across the supply chain.
Securing Your GitHub Actions — Jaroslav Lobacevski (GitHub) talked about common GitHub Actions vulnerability patterns that the GitHub Security Lab team has seen in the wild and offers a set of best practices and tools to prevent them from occurring in your own CI/CD supply chain.
AIxCC Results and New Open Source AI Projects To Help Secure Open Source Software — Jeff Diecks (Linux Foundation) reflected on the outcomes and new projects sparked by the AIxCC initiative.
Tamper-Proof ML Metadata via Model Signing Initiative — Mihai Maruseac (Google) presented how Model Signing enables verifiable claims about ML models and datasets, laying a foundation for AI supply chain security.
Security Risks Related to Downloading and Running LLMs Locally — Florencio Cano Gabarda (Red Hat) identified the risks of executable formats in ML models and controls to mitigate them.
Trends and Insights From the Sigstore Ecosystem — Eve Martin-Jones (Google) shared empirical insights into how Sigstore is used across projects to build trust through transparency logs and short-lived credentials.
Applying the OpenSSF Threat Model: Lessons from Ericsson — Georg Kunz and Jussi Auvinen (Ericsson) discussed how threat models are mapped to ISO 27001 and used to guide mitigation efforts in enterprise settings.
A New Frontier: The Future of Quantum-Safe Software Supply Chains With Sigstore — Arthur Savage (Red Hat) outlined the steps required for post-quantum readiness in software supply chains and the role of Sigstore in supporting that transition.
SBOM at Scale: Securing Eclipse Foundation Projects With Automated Supply-Chain Visibility — Mikael Barbero and Kairo Araujo (Eclipse Foundation) demonstrated how Eclipse integrates SBOMs into delivery pipelines, preparing for regulatory requirements and potential vulnerabilities.
The day concluded with the Keynote: Closing Remarks from OpenSSF General Manager Steve Fernandez, who thanked the community for their continued contributions and celebrated the wins achieved together. He acknowledged that it is the collective effort of speakers, contributors, and attendees that makes this progress possible. Your collaboration and passion drive open source security forward every day.
Special thanks to all of our speakers for sharing expertise and sparking conversations that shape the future of securing open source.
We also thank our sponsors Kusari and Red Hat for supporting the event’s break and community reception. Your partnership helps bring our community together.
 Inside the Incident: Tabletop Exercise at OpenSSF Community Day EU
Inside the Incident: Tabletop Exercise at OpenSSF Community Day EU
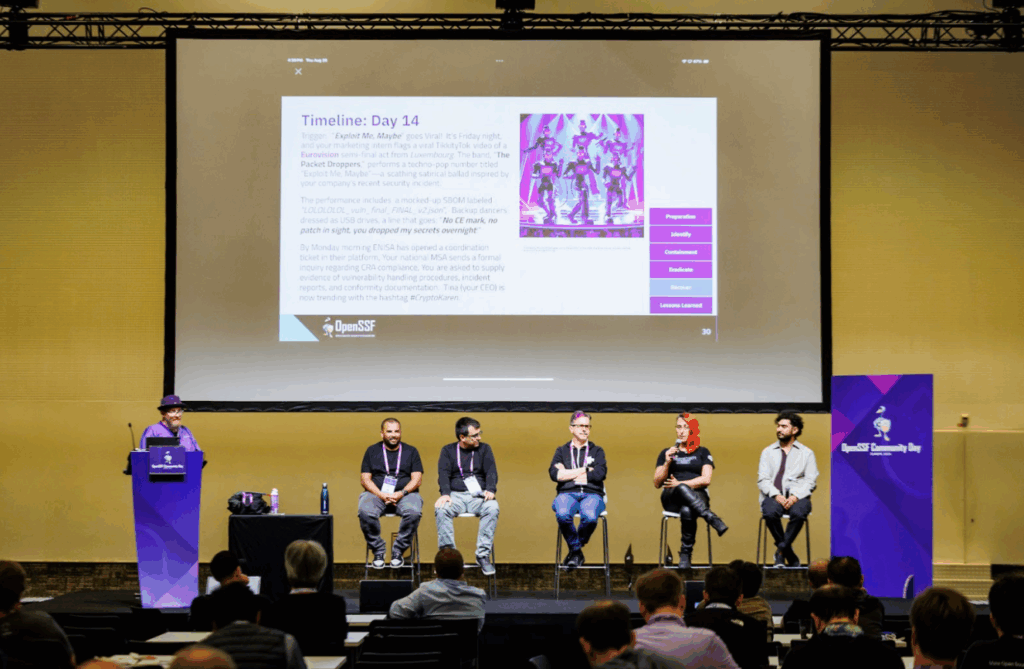
One of the most engaging and practical sessions of OpenSSF Community Day Europe was the interactive Tabletop Exercise (TTX), moderated by Christopher “CRob” Robinson (OpenSSF). Designed as a “mock disaster”, this live simulation walked attendees through the lifecycle of a security incident, mirroring real-world challenges faced across the open source ecosystem.
The scenario centered around the fictional Fluffernutter project and its integration across the software supply chain. The panelists assumed diverse roles across that chain:
- Kairo Araujo (Eclipse Foundation) as an upstream OSS maintainer
- Amir Montazery (OSTIF) as a CISO at LargeCo
- Daniel Appelquist as an OSPO lead at LargeCo
- Florencio Cano Gabarda (Red Hat) as a downstream customer
- Æva Black as a national coordinator
The panel navigated each phase of the incident response lifecycle:
- Preparation
- Identification
- Containment
- Eradication
- Recovery
- Lessons Learned
Throughout the session, participants demonstrated how different organizational roles interact under pressure and must collaborate effectively to resolve threats.
The collaborative debrief that followed surfaced critical takeaways:
- Common coordination gaps between upstream and downstream stakeholders
- The need for clear SBOM and vulnerability communication channels
- How OpenSSF tools (like sigstore, GUAC, and SLSA) can support rapid response
This exercise brought real-world urgency to the room and helped participants understand how to apply practical frameworks in their own organizations. It served as both a learning lab and a policy-technical bridge, highlighting that preparedness is not just technical, but deeply organizational and human.
The TTX will remain a flagship engagement model for future OpenSSF Community Days, equipping the open source ecosystem with both the tools and mindsets needed to strengthen global software resilience.
 Looking Ahead
Looking Ahead
In the coming months, translation of these conversations into actionable outcomes will be key:
- Register now for OpenSSF Community Day Korea in Seoul on November 4 and Open Source Security Con in Atlanta on November 10. These events continue the global momentum toward better open source security practices.
- Watch for session recordings on the Linux Foundation and OpenSSF YouTube channels.
- Photos are available on flickr.
- Explore publications on CRA readiness, such as the August 2025 Linux Foundation Research reports: Open Source as Europe’s Strategic Advantage highlighting the lesson of the EU CRA, Unaware and Uncertain: The Stark Realities of Cyber Resilience Act Readiness in Open Source; Pathways to Cybersecurity Best Practices in Open Source
- Join us in Europe this fall:
- Linux Foundation Europe Member Summit (Oct 28)
- Linux Foundation Europe Roadshow in Ghent (Oct 29), featuring the CRA in Practice: Secure Maintenance track
- European Open Source Security Forum, co-hosted with CEPS in Brussels (Oct 30), bringing together open source leaders, policymakers, and security experts
- Join us in upcoming working groups and get involved!
Conclusion
Open Source Summit Europe and OpenSSF Community Day Europe 2025 delivered a vibrant blend of policy foresight, technical deep dives, collaborative tools, and hands-on preparedness that highlighted the open source security community’s unwavering commitment to resilience and innovation. Whether you’re embedding from the ground up, policing transparency, or governing global supply chains, there was something at every track to spark your journey forward!
