By: Oliver Chang (Google), Navid Emamdoost (Google), Adam Korczynski (ADA Logics), and David Korczynski (ADA Logics)
In recent years, many development workflows have come to rely on fuzzing, an automated technique for finding bugs by feeding unexpected inputs into software with the intent to trigger crashes or other problems. Fuzzing plays an important role in vulnerability discovery and supports one of the OpenSSF’s main goals of improving vulnerability detection and response for open source software. However, the effectiveness of fuzzing depends on how much of the code is covered by it, and writing effective tools to implement fuzzing (“fuzzers”) with good coverage is still challenging. Fuzzing today often hits coverage roadblocks (“blockers”) that prevent effective fuzzing of some code areas. Today these require manual analysis to identify and unblock, and there has been no easy or consistent way to perform this analysis. Recent notable vulnerabilities such as BigSig and NSO iMessage show that there is still room for improvement in fuzzing of projects, even in projects already applying regular fuzzing.
To address some of these issues, we are excited to announce an initial release of Fuzz Introspector, a collaborative effort from OpenSSF members. Fuzz Introspector provides actionable insights for developers to identify fuzzing coverage blockers by analyzing functions, static call graphs, and runtime coverage information. Resolving these blockers will help unlock improved fuzzing coverage, resulting in more vulnerability discoveries and greater confidence for users in the reliability of the code they fuzz. It can be used by two different kinds of developer: (1) developers of projects that use fuzzing (enabling them to have improved fuzzing results), and (2) developers of fuzzers (enabling all users of those fuzzers to have improved fuzzing results).
Currently, Fuzz Introspector supports C/C++ projects. For each project, Fuzz Introspector provides:
- a detailed overview of all functions in the projects, including their coverage, reachability and complexity;
- a statically extracted call-tree overview overlayed with runtime coverage information for each fuzz target along with a blocker table to pinpoint roadblocks for each fuzz target;
- a list of suggested optimal fuzz targets that can be added to increase coverage.
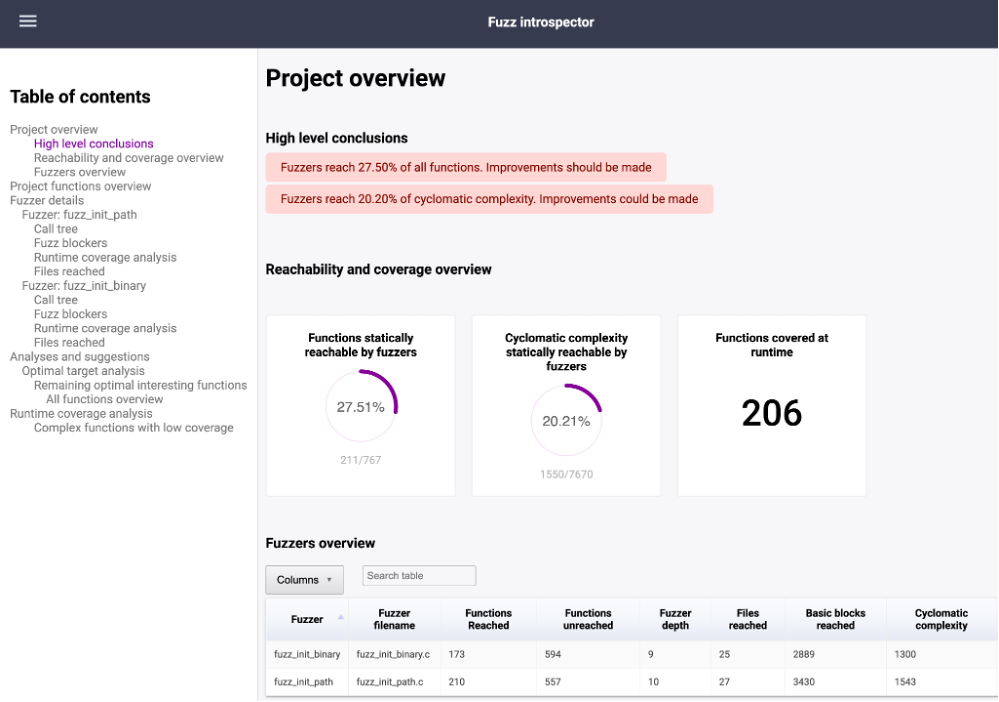
One early milestone for Fuzz Introspector was its recent integration into the free OSS-Fuzz service, with reports publicly accessible via the public index or accessible to OSS-Fuzz project maintainers via the OSS-Fuzz project homepage. As part of this development, we used the results of Fuzz Introspector to improve multiple OSS-Fuzz projects, including directly addressing a gap in the xpdf project detailed in a blog post by Google Project Zero. You can find more examples of reports and how they were used to improve our projects in the project repository.
Fuzz Introspector is being actively developed. Some plans for the future include supporting more programming languages, improving the precision of coverage blocker identification, and guiding automated coverage exploration beyond blockers (to enable more automated elimination of blockers). We welcome community contributions toward these goals and encourage anyone interested in getting involved to take a look at the current reports, help improve fuzz targets, and provide feedback via https://github.com/ossf/fuzz-introspector. With collaborative effort, we hope that Fuzz Introspector will offer developers of fuzzers an easier way of evaluating and improving their fuzzers, making this vulnerability detection technique more effective for the wider open source community.