Authors: Best Practices Working Group, Laurent Simon (Google), Azeem Shaikh (Google), and Jose Palafox (GitHub)
Today, two members of the Open Source Security Foundation, Google and GitHub, are partnering to release Scorecards V4, featuring a new GitHub Action, an added security check, and scaled up scans of the open source ecosystem.
The Scorecards project was launched last year as an automated security tool to help open source users understand the risks of the dependencies they consume. Though the world runs on open source software, many open source projects engage in at least one risky behavior—for example, not enabling branch protection, not pinning dependencies, or not enabling automatic dependency updates. Scorecards makes it simple to evaluate a package before consuming it: a scan run with a single line of code returns individual scores from 0 to 10 rating each individual security practice (“checks”) for the project and an aggregate score for the project’s overall security. Today’s release of a Scorecards GitHub Action makes it easier than ever for developers to stay on top of their security posture.
Helping Developers
Scorecards GitHub Workflow Action
Previously, Scorecards needed to be run manually to judge how changes to a project affected its security. The new Scorecards GitHub Action automates this process: once installed, the Action runs a Scorecards scan after any repository change. Maintainers can view security alerts in GitHub’s scanning dashboard and remediate any risky supply-chain practices introduced by the change.
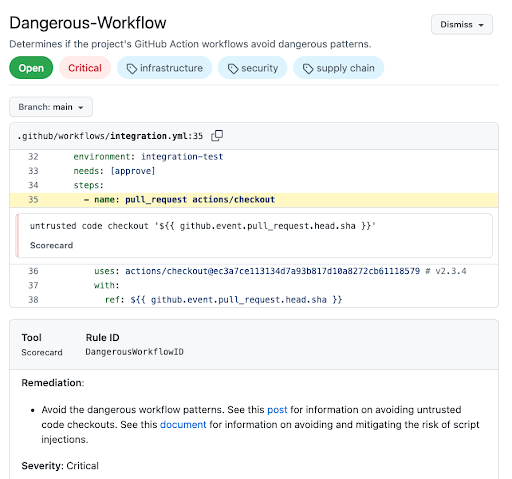
As shown in the example above, each alert includes the severity of the risk (low, medium, high, or critical), the file and line where the problem occurs (if applicable), and the remediation steps to fix the issue.
Several critical open source projects have already adopted the Scorecards Action, including Envoy, distroless, cosign, rekor, kaniko. The Action is free to use and can be installed on any public repository by following these directions.
New Checks
We’re continually adding new security checks to help developers assess risks to their projects. This release adds the License check, which detects the presence of a project license, and the Dangerous-Workflow check, which detects dangerous usage of the pull_request_target trigger and risks of script injections in GitHub workflows. Dangerous Workflow is the first Scorecards check with a “Critical” risk level rating, since these patterns are so easily exploited—with these workflows, a single pull request can introduce compromised code into a project. The new Scorecards check informs users of the existence of these vulnerabilities in their project and provides remediation guidance to fix the issue.
Scaling Up Data Availability
The Scorecards team runs weekly scans of a set of critical open source projects, creating snapshots of the security of the overall open source ecosystem at any given time. Over the past few months, we have increased the scale of scans from 50,000 projects to one million projects identified as most critical based on their number of direct dependencies, giving a more detailed view of the ecosystem and strengthening supply chain security as users see improved coverage of their dependencies. With Scorecards V4, the weekly scans now reflect the 0-10 rating scale for each repository rather than the pass-fail results of previous versions, adding more granularity to the data. The scan results are publicly available through the Scorecards API and on the OpenSSF metrics dashboard and Open Source Insights partner websites.
Growing the Community
Since our initial launch, we have been improving our codebase thanks to the expanding Scorecards community. In 2021, we grew to over 40 unique contributors, averaged over 16 commits per week (totalling 860 commits), and closed 270 issues. We warmly welcome new contributors; check out this list of good first-timer issues if you’d like to join in the fun.
Here’s a few examples of projects that have adopted Scorecards:
“kaniko is a popular open source container image builder for Kubernetes, so it’s very important to maintain the security of the repository and the codebase. The ossf/scorecard Github Action takes care of this for us and continuously monitors the repository. It took less than 5 minutes to install and quickly analyzed the repo and identified easy ways to make the project more secure.”
– Priya Wadhwa, Kaniko
“We rely on scorecards in distroless to ensure we follow secure development best practices. Secure source and config means safer base images for all our users.”
– Appu Goundan, Distroless
“Scorecards provides us the ability to rapidly litmus test new dependencies in the Envoy project. We have found this a valuable step in vetting new dependencies for well known attributes and we have integrated Scorecards into our dependency acceptance criteria. Machine checkable properties are an essential part of a sound security process.”
– Harvey Tuch, Envoy
Strengthening the Supply Chain
We expect 2022 to be a year of growing awareness of the criticality of supply chain security. If your New Year’s resolution is to pay closer attention to your projects’ security, using the Scorecards GitHub Action is one of the easiest ways to get started. Just install the workflow on your repositories and follow the remediations instructions to address the issues that roll in. Each incremental improvement helps strengthen the open source ecosystem for everyone.
For additional information, head over to the release notes and, as always, please reach out with any questions or suggestions.